Modernize apps or IDPs
Switch clouds, scale your architecture, swap out a new IDP, or deploy the next big thing so you can build a more resilient, efficient business — without touching your apps.
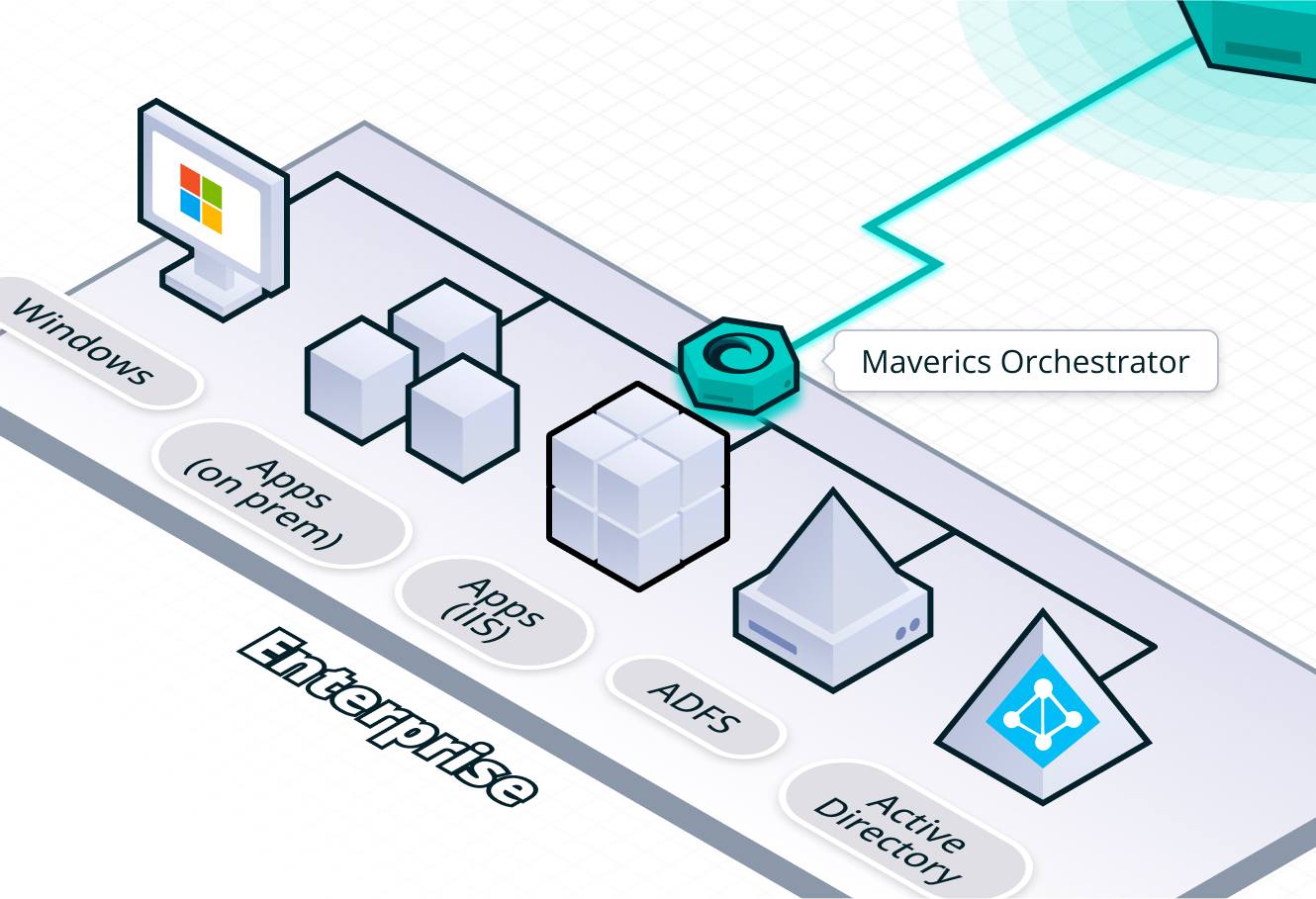
Modernize Windows web apps off Active Directory
Using Active Directory for user authentication used to make sense — that’s why it was ubiquitous for both forms-based authentication and as an IDP. But these days, it comes with baggage: Active Directory has to be on-prem and it has to be actively managed. A cloud-based IDP — like Microsoft Entra ID — doesn’t need active management. The problem is that — traditionally, at least — modernizing off Active Directory involved extensive app rewrites. But modernizing with Maverics does not.
Here’s how it works: Instead of rewriting every app that relies on Active Directory, you can put Maverics in its place and then use any modern IDP to authenticate and authorize users. In the case of SASL-bound apps using NTLM, Maverics uses a “facade” that makes the app believe that the user sessions and identity data is flowing from your Active Directory. This means apps don’t need any individual code changes because what they’re seeing stays the same. And because Maverics just drops into your network, it doesn’t need to join a domain.
This Maverics Active Directory Authentication Facade supports GSS-SPNEGO (NTLM) with user authentication with passwords. The facade also provides attributes and user context such as Roles, Groups, and Attributes. This allows you to handle the End Of Life of NTLM and securely swap it out for cloud identity or other strong authentication — without rewrites, making it ideal for previously ‘unmanageable’ apps.
Natively support Windows Kerberos and IWA authentication
Stop forcing users to double authenticate — enable them to access any app using their initial IWA login authentication instead. Extending authentication this way with Maverics reduces friction by only making users log in once and then securely translating session tokens into whatever type is needed by your apps.
Here’s how it works: Windows desktop can seamlessly access apps secured by Maverics because the proprietary Maverics Windows Client Authenticator (IWA) securely validates users’ sessions. This keeps users logged in and happy.
Secure Windows web apps on IIS
The ubiquitous IIS web server hosts millions of Microsoft web apps but it doesn’t easily support modern authentication services like Multi-Factor Authentication (MFA) and cloud-based identity providers. That’s where Maverics comes in.
Maverics integrates with IIS to bring the security of modern authentication services to IIS-based apps. This way, you can point authentication for IIS apps and users away from Active Directory and to Microsoft Entra ID or any other IDP like Okta or CyberArk.
Modernize ADFS apps to cloud identity
Support for Active Directory Federation Services (ADFS) is coming to end-of-life — and modernizing business-critical apps off it is anything but simple. If time, budget and tech debt were not an object, the best way to leave ADFS would be by refactoring every app it supports. However, this swallows up hard to find developer resources.
Alternatively, you can take a standards-based approach with Maverics and authenticate users of ADFS apps with OIDC, SAML and even passwordless authentication.
Modernize from legacy WAM to Microsoft Entra ID
Ready to move off of Siteminder, Oracle, Ping or ForgeRock and onto modern Entra ID? Retire your outdated Web Access Management (WAM) vendor for good and get rid of unreasonable license fees and support costs — without rewriting any of your applications.
Use these simple step-by-step recipes to quickly modernize from legacy services to Microsoft Entra ID.
Extend Microsoft Entra ID to secure on-prem Windows web apps
Enable seamless co-existence of your old and new identity systems. This way, you can gradually modernize every app and move some to the cloud without interrupting access or creating tech debt.
Help Microsoft Entra ID and legacy Active Directory peacefully coexist
Even if it’s not the best authentication method, your ubiquitous Active Directory still holds valuable user data and attributes. That’s why Maverics supports coexistence between your legacy Active Directory and your modern cloud identity.
Here’s how it works: Maverics lets you select which IDPs users authenticate with. This way, you can configure Maverics to authenticate users differently based on who they are: for example, you can authenticate employees using your on-prem Active Directory and authenticate partners and customers in Microsoft Entra ID.
Transform legacy Windows sessions into cloud identity sessions
On-premises Windows web apps expect user identities to be presented using IWA Kerberos or the older NTLM. However, modern identity services use standards like OIDC and SAML.
Maverics allows Windows web apps to use modern services by transforming a IWA Kerberos session into a SAML or OIDC session. This way, users can access cloud apps seamlessly. Maverics also works with headers, and can turn OIDC claims and SAML assertions into HTTP Headers passed to an authorization service.
Secure hybrid on-prem apps with Microsoft Entra ID
Enterprises have multiple web applications that need to remain on-premises but require the protection of modern authentication services.
Maverics can extend Microsoft Entra ID to on-premises apps so that you can quickly secure Windows web apps running in your on-prem data center.
Extend Microsoft Authenticator to on-prem apps
Passwords are an enormous liability but adding a modern MFA solution to an on-prem Windows web app usually means refactoring. It doesn’t have to.
Maverics can extend Microsoft Entra ID authentication to any web app — including your ‘unmanageable’ on-prem ones — without code rewrites. On top of this, Maverics enables backup MFA options so that if users lose their primary authentication method (e.g. users forget their phone and the mobile authenticator on it), they can use an alternative strong authentication option.
Extend non-Microsoft MFA to on-prem Windows apps
Modernize any Window app with any MFA provider you want — without refactoring. Use these recipes to get started.
Don’t take the hard path to modernization by building custom Microsoft Entra ID integrations or needlessly refactoring apps
Maverics integrates all your multi-generational Microsoft services into your identity fabric. Your organization is already committed to Microsoft — so make app onboarding and modernization easier with Maverics.
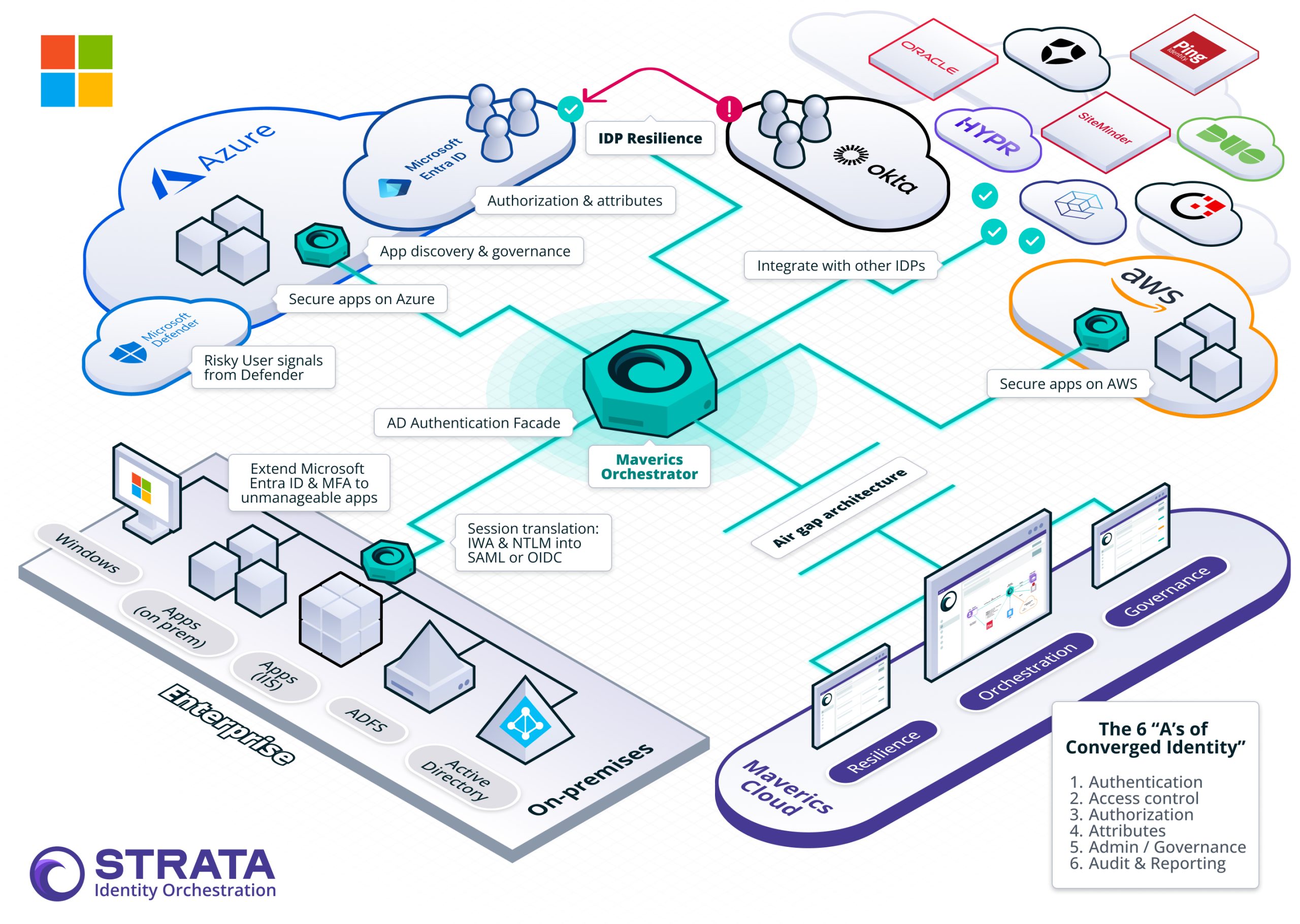
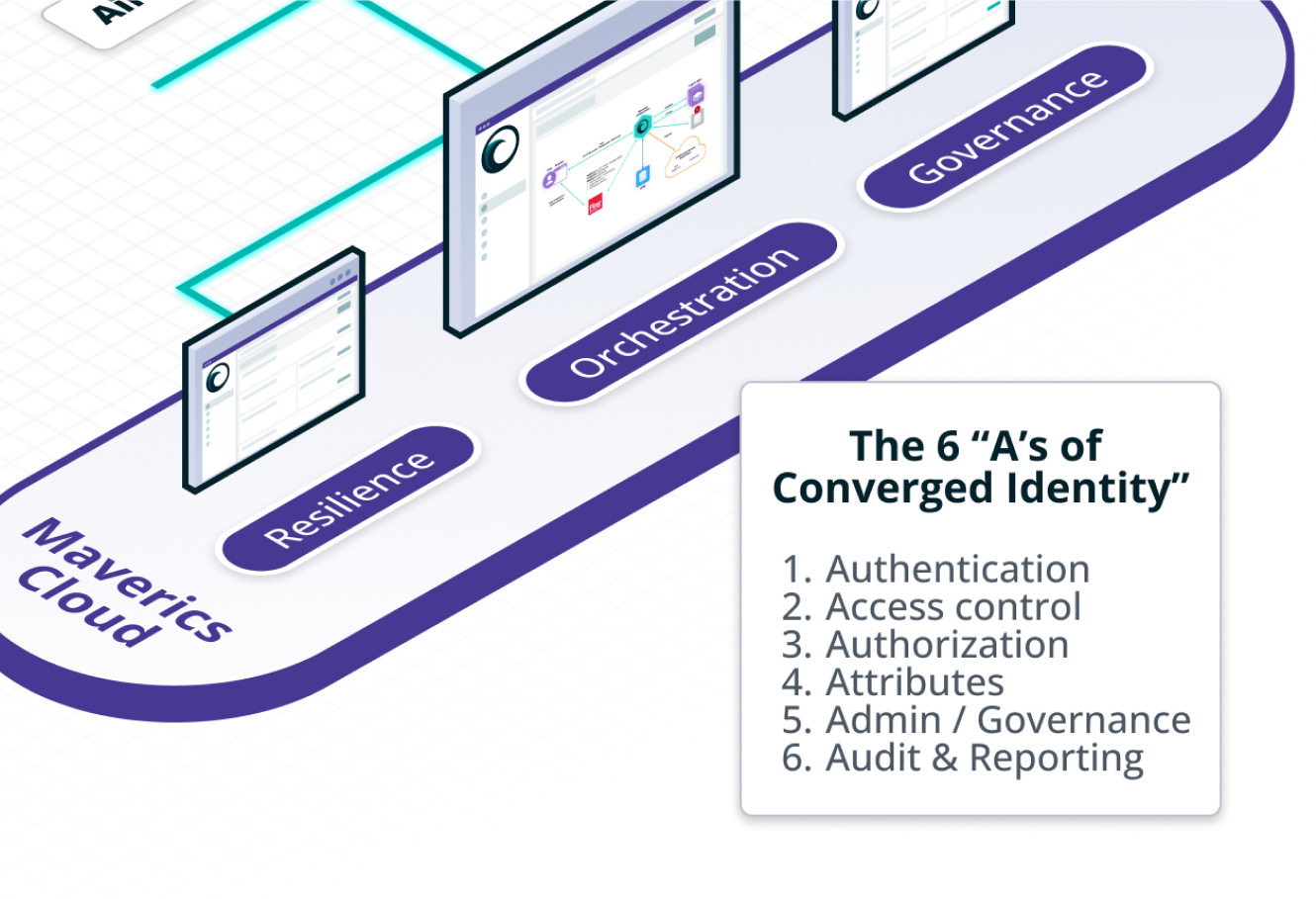
Maverics supports all the ‘A’s of Microsoft Identity’
Maverics brings all the crucial parts of identity into a single orchestration platform, so you can do it all:
- Authenticate users with Microsoft Entra ID and Microsoft Authenticator protection.
- Enforce Access Control with Entra ID Roles, Groups, and Attributes.
- Define Authorization policies that use Azure Defender fraud detection and Risky User signals.
- Pull disparate Attributes & tokens from Microsoft Entra ID, Active Directory, and third-party attribute stores.
- See every app and policy on Azure with Administration & governance
- Audit & report on cross-environment user activities on-prem and in the cloud
Run Maverics Orchestrators on Microsoft
Maverics is built to take advantage of the scalability and rich feature set of both the Azure cloud platform and Windows environments.
You can run the Maverics Orchestrator on an on-prem Windows server or on the Azure cloud. Maverics can optionally be run on Azure Kubernetes Services (AKS).
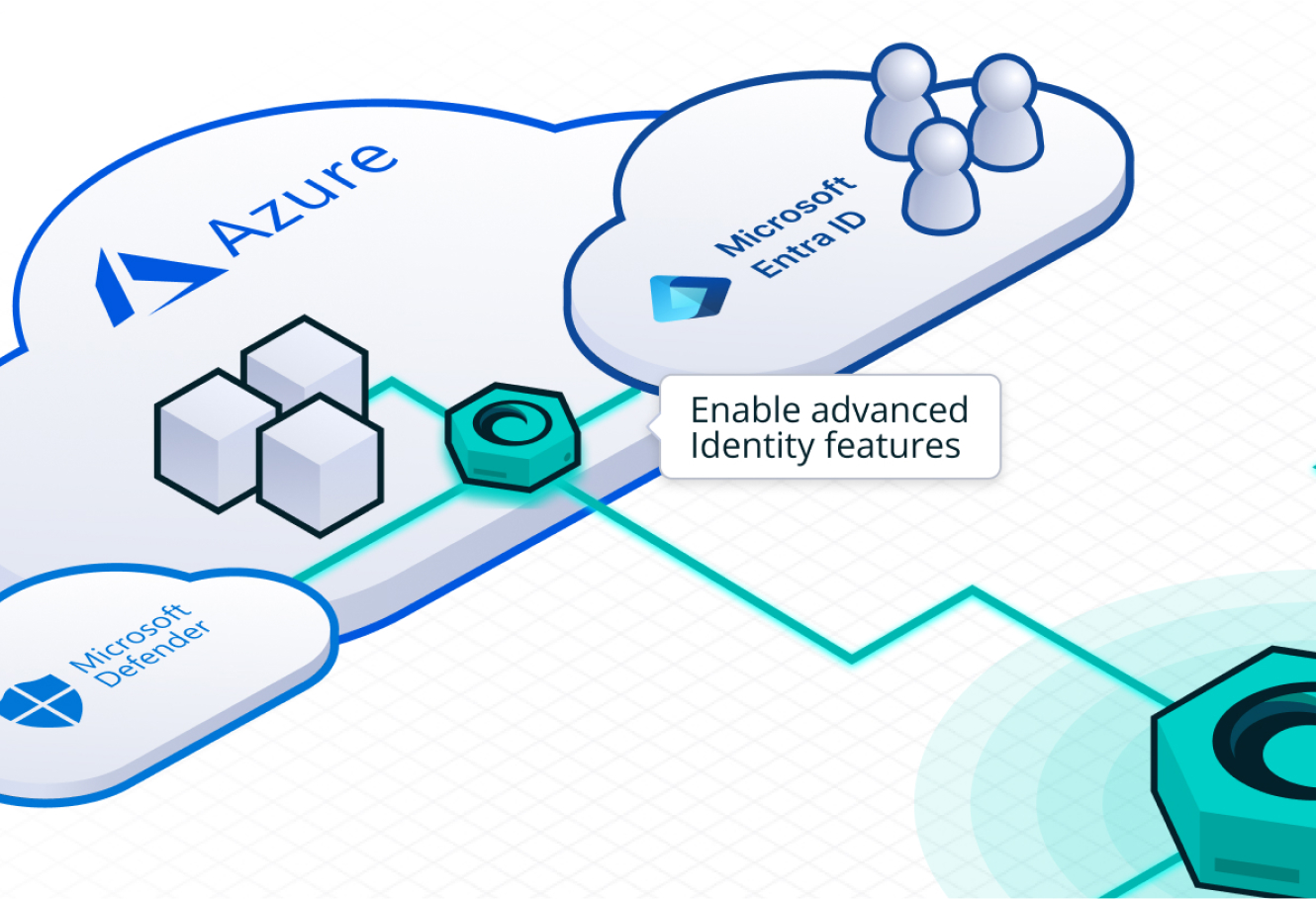
Bolster ‘Microsoft Entra ID for Customers’ with advanced identity features
Microsoft Entra ID for customers (Azure AD B2C) CIAM trades advanced features for low cost. If you’re already leveraging other Microsoft products, using it just makes sense. With Maverics, you can add new features like conditional access, authorization, multi-step user onboarding flows.