THE STATE OF MULTI-CLOUD 2023
Complexity is the enemy of securing identity
The multi-cloud, multi-IDP world is evolving: 79% of enterprises now use 2+ IDPs. (That’s an 18% increase from 2022.) That’s not the only change.
To understand what’s happening, we surveyed 300+ identity practitioners and leaders. And we summed up the key 2023 trends for identity authentication and authorization in this report.
Get the Report today
Organizational challenges, by the numbers
76%
Have limited visibility into access policies & applications
64%
Lack integrations between cloud identity & on-premises apps
78%
Struggle with identity modernization barriers like source code & resourcing
Identity fragmentation is hurting every team:
- Identity teams need enhanced interoperability within distributed infrastructures and yet struggle with visibility
- End-users need seamless authentication experience across applications so they can get the job done
- Bandwidth-strapped identity practitioners are stretched thin with maintenance tasks
- Teams look to hire more experts and yet skilled cybersecurity professionals are hard to find
All these problems need to be solved. Urgently.
Download the 2023 report today and discover the original research that digs deep into the challenges and outlines the opportunities ahead.

TRUSTED BY
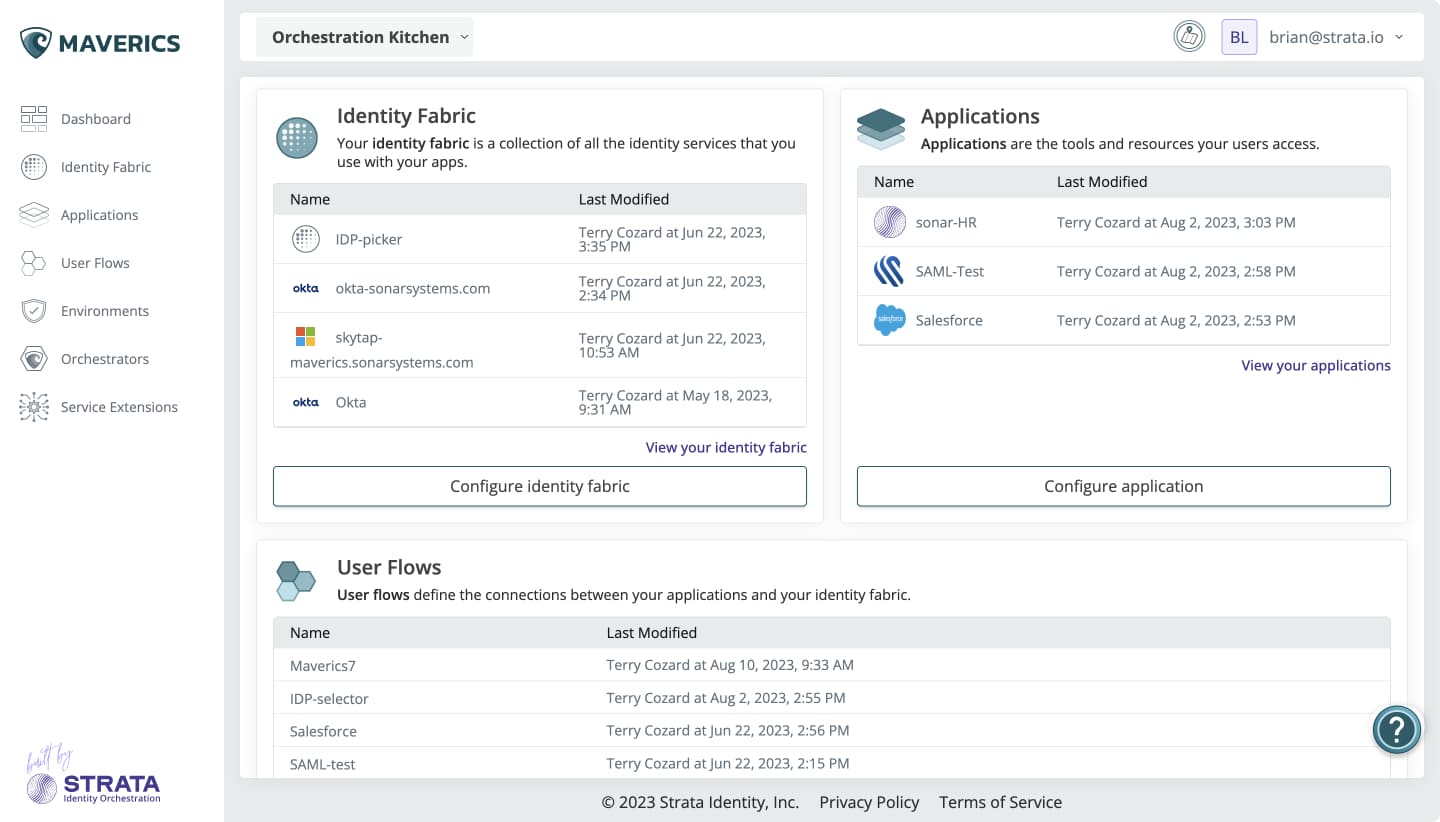
About Strata
Strata is the leader in Identity Orchestration with its platform, Maverics, as the only solution built for today’s multi-cloud and hybrid-cloud environments. Strata’s distributed approach enables organizations to modernize identity and break decades-old vendor lock-in easily and empowers them to migrate enterprise workloads to the public cloud.