Identity Fabric
What is an identity fabric and why do you need one?

As cloud migration and digital transformation reach new levels of ubiquity, it’s clear that multi-cloud and hybrid cloud environments allow for greater speed, agility, and security. However, multiple clouds mean more significant challenges. One of the biggest hurdles to arise is how to secure legacy applications consistently across clouds and on-premises.
The reality is that modern security tools such as multi-factor (MFA) or passwordless authentication can’t be used on legacy or non-standards-based apps. Making apps secure in the cloud(s) traditionally means manually recoding each one, which is time-intensive and costly and redirects valuable IT resources from innovation.
A critical part of going multi-cloud means managing the new identity silos that come with each cloud. Distributed identity empowers you to manage identity and policies across multiple clouds consistently.
We call this new distributed identity model an identity fabric.
RELATED READING: WHAT IS IDENTITY ORCHESTRATION?
What is an identity fabric?
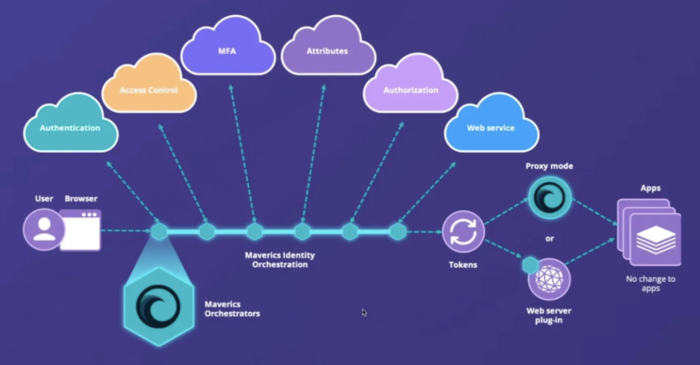
An identity fabric is an abstraction layer in a multi-cloud identity management framework and is part of Identity Orchestration software.
The identity fabric uses orchestration to manage multiple identity domains on multiple clouds.
It also uses abstraction to:
- Manage identity across any IDP (both on-premises and cloud-based)
- Access policies across cloud vendors
- Avoid rewriting apps to speak modern protocols
- Offer a no-code integration that eliminates custom coding
In other words, an identity fabric enables the orchestration of distributed environments, allowing for consistent identity and access to policy management across the network.
How does an identity fabric work?
It starts with the abstraction layer, which inventories and maps the elements of the extended identity system across multiple clouds. As a connecting layer that enables the orchestration of disparate environments, an identity fabric has interwoven threads connecting legacy infrastructures with cloud-based assets. The identity fabric enables consistent identity and access policy management for multi-cloud and hybrid clouds.
The identity fabric abstraction layer unifies distributed identity providers and infrastructures like MFA, directories, databases, APIs, authentication, and authorization providers. Developers can use a single abstracted API for the entire range of connected systems, enabling consistent identity and access across multiple clouds and vendors.
With no-code or low-code integration, an identity fabric eliminates the need to custom-code identity into apps for cloud deployment. IT teams can use a configuration approach to ‘wire’ apps and identity, making it possible to switch one identity provider out for another easily and without coding. Or, they can roll out a new identity service — like passwordless, for example — to apps without rewriting the app.
Why is an identity fabric needed in multi-cloud? What problems does it solve?
Navigating identity and access management (IAM) within multi-cloud and hybrid cloud environments can feel like steering through a dense fog. Without clear visibility, risks increase – including security breaches and costly consequences.
An identity fabric breaks identity lock-in, unifies fragmentation, reduces risk, and enables agility and choice across clouds.
It’s like your lighthouse, allowing you to see through the complexity to solve crucial problems, such as:
Identity lock-in
Identity vendor lock-in is common in IAM and can add an extra layer of frustration for IT leaders seeking to update their systems due to policy compliance reasons or other business drivers.
Identity lock-in occurs when apps integrated with legacy identity systems use outdated ‘cookie’ sessions. Moving off this model requires rewriting apps to work with a new identity system, taking months of developer time. In turn, this locks organizations into the legacy platform that legacy identity runs on, preventing apps from moving to the cloud.
Fragmentation & silos
Organizations using more than one cloud must contend with identity fragmentation. Fragmented identity silos and manual IAM for critical infrastructure puts constraints on your business.
An identity fabric enables consistent identity and access policies to be implemented across disparate clouds and platforms.
Cybersecurity threats
Cybercriminals are getting bolder and more sophisticated. But they still go after the low-hanging fruit first — even criminals know there’s value in keeping it simple. The 2023 Verizon Data Breach Investigation Report found that 86% of data breaches involved the use of stolen credentials. Weak passwords and poorly protected passwords are arguably the weakest links.
With the distributed nature of the cloud — and now multiple clouds — a new approach to managing identity is needed.
While there’s no substitute for robust threat detection systems, the capacity to instantly deploy IAM updates and enforce policy changes ensures that vulnerabilities are quickly addressed. Cybersecurity and IAM are now intrinsically connected across all areas of an organization.
Agility
An identity fabric enables organizations to decouple their infrastructure from their apps, making it possible to easily move apps and workloads across clouds using whatever identity system makes the most sense for the use case.
Benefits of using a distributed identity fabric
We’ve addressed how an identity fabric directly addresses the challenges of fragmented identities, vendor lock-in, and security vulnerabilities. Let’s take a further look at some of the other key benefits an identity fabric brings to an organization.
1. Fix identity fragmentation
An identity fabric can help you integrate silos of identity across different cloud platforms and on-prem systems, enabling you to enforce consistent policies across multiple cloud platforms.
2. Break vendor lock-in and enjoy agility and choice
With an identity abstraction layer that enables you to use the cloud platform and identity solution of your choice while eliminating the need to rewrite apps when migrating identity systems.
3. Reduce costs for identity
Reduce the costs of rewriting apps to work with different identity systems. Reduce costs for moving platforms and integrating identity with apps. Save millions in measurable hard costs.
4. Speed up identity projects
Automate identity workflows like authentication, access control, migration, and last-mile integration across different identity platforms—on-prem and in the cloud. Using automation and orchestration instead of custom code can cut project timelines by more than 85%. Speed work-from-home deployments by rapidly making apps available outside the firewall.
5. Zero-touch deployments
Drop-in implementation means no disruptions to apps, infrastructure, or user experience. Zero-code connector integrations eliminate custom code.
6. Distributed, multi-cloud identity support
Support multi-cloud distributed apps that require consistent identity across multiple clouds.
7. Improve security by eliminating identity silos
Tapping advanced security features like MFA, passwordless, GDPR privacy, etc.
Protect your infrastructure against cyberattacks with Identity Fabric Immunity
Identity fabric immunity refers to the resilience of your identity infrastructure against targeted cyberattacks and internal vulnerabilities. Resilience stems from the decentralized nature of the fabric, coupled with robust security mechanisms.
Key Identity Fabric Immunity Principles:
- Zero Trust: Continuously verifying user identity and privileges.
- Least Privilege: Granting only the minimum access required to perform tasks.
- Multi-Factor Authentication (MFA): Enforcing multiple verification factors.
- Context-Aware Access: Considering device, location, and behavioral patterns.
- Continuous Monitoring: Detecting and responding to anomalous activities.
How does an identity fabric strengthen immunity?
An identity fabric, through its architecture and features, enables the implementation of these principles across a diverse IT and cloud landscape. It also provides the tools to centralize policies, automate access control, and enforce security consistently across your entire infrastructure — reducing human error and limiting the impact of any single point of compromise.
What solutions does Strata Identity offer?
Whether you’re seeking to migrate your entire network to the cloud in the short term or want a gradual but efficient transition for some of your key assets, Strata’s Maverics Identity Orchestration Platform can help you to reach your goals without compromising user experience or incurring costs of labor-intensive rewrites of code. Regardless of the complexity of your business or the sensitivity or scale of your operations, there is a simple way to shift to the leading edge of multi-cloud identity trends.
Read on for additional solutions Strata offers:
- Distributed identity management: Distributed identity management allows you to consistently manage identity and access apps across multiple identity systems running on many platforms. The Identity Fabric is not another SSO or IDP.
- Decouple apps & identity domains: The identity abstraction layer replaces the 1:1 app-to-identity integration model, replacing it with a 1-to-ANY model. This decouples apps and identity domains to allow you to mix and match identity systems without rewriting apps.
- Automated Identity Orchestration: Identity Orchestration enables the automation of identity processes like authentication, access control, migration, and last-mile integration, using zero-code connectors.
- Manage identities & policies across clouds: Identity integration using one API for managing identities and policies across clouds. Further leverage a broad catalog of zero-code identity connectors, including AWS, Azure, Azure AD, Okta, Ping, CA SiteMinder, Oracle Access Manager, Active Directory, and others both in the cloud and on-prem.
- Build apps to work on-prem & across clouds: Distributed identity architecture built natively to work on multiple clouds and on-prem. Enables you to build distributed apps that span multiple clouds by unifying disparate identity systems to enable an app to be composed across multiple clouds.
- Manage policy consistently any IDP: Single Pane of Glass that visualizes the discovered apps and identity domains that make up your identity fabric. Create an inventory of identity software, user repositories, apps, and configurations across on-premises and public clouds; take full control of your enterprise identity and access management and save months of manual effort to inventory and analyze identity infrastructure.
Ready to make identity consistent?
The IT team and CFO are not the only winners with Identity Orchestration. Customers, vendors, and employees across the company benefit from increased openness in your system while contributing to a secure network.
See how you can start building your identity fabric today using the existing identity services you have — and make them work together so much better!
Modernize any app with any IDP in minutes. Join the 'Orchestration Kitchen' workshops.