
The team at Strata loves nothing better than a challenge. After all, the company was founded on the philosophy of making the impossible possible. So, like...

5 best practices to smoothly transition identity providers from an acquired company Mergers and acquisitions (M&A) are crucial in growing and expanding businesses. Some big reasons...

Data sovereignty is rapidly becoming one of the biggest challenges in identity and access management for multinational organizations. Managing and enforcing who can access what data...

“We weren’t looking for three or four tools that would be best of breed to try to make this all work. We wanted one single tool...

“Many apps simply can’t be rewritten, making the manual approach impractical from a timing and cost standpoint. ” Eric Olden, CEO and Co-founder at Strata Identity...

Adding passwordless authentication is on the short list of identity priorities in 2023 for many organizations. Yet, it’s not as simple as picking a solution and...

Why it’s time to move on from your outdated identity provider The modern digital landscape is expanding and transforming at breakneck speed. As a result, the...

Key insights and highlights from the State of Multi-Cloud Identity Report 2023 As digital transformation rapidly reshapes the business landscape, multi-cloud strategies are becoming the norm...

The first step in achieving success is recognizing that a merger or acquisition changes processes, webpages, apps, and logins. Although this may seem obvious, what often...

In today’s rapidly evolving business environment, enterprise applications are crucial for driving innovation and productivity. They are the lifeblood of the modern organization and are relied upon...

Imagine you’re a software developer in a large organization. You’ve just spent months, maybe even years, rewriting code for hundreds of applications to meet the latest...

Authorization is at the foundation of modern security and one of the keys to zero trust. On Tuesday, Amazon Web Services (AWS) made Amazon Verified Permissions...

With cloud modernization, one of the most significant challenges for app owners is managing identity and authentication, which can divert attention from creating an exceptional product....

There’s a common thought that if an application speaks industry-leading identity standards, it automatically makes it modern. However, the requirements of apps today go beyond that....
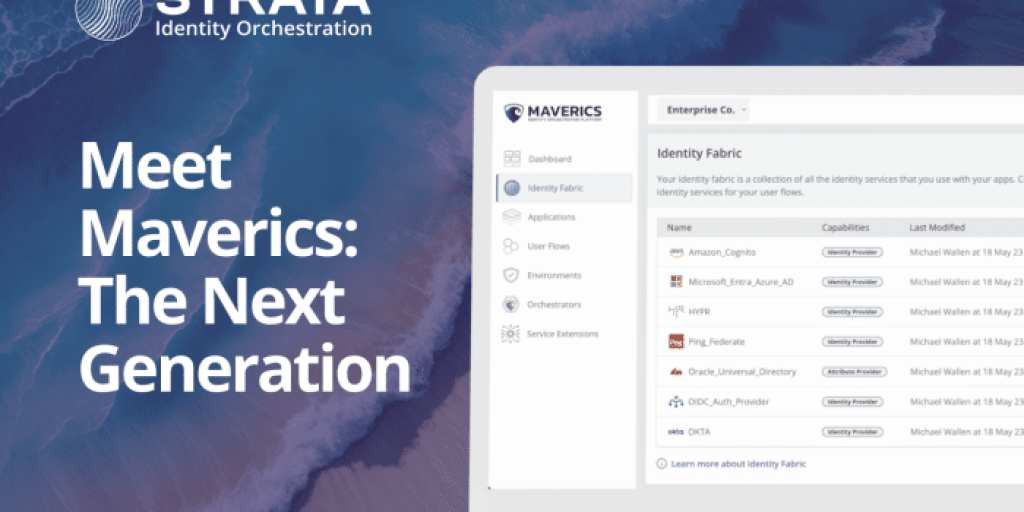
Trailblazing Identity Orchestration for enterprises “Maverics is the only Identity Orchestration platform that allows enterprises to mix and match incompatible identity systems without rewriting each application...

With increased cloud migration and the adoption of cloud-based apps, Cloud Security Architects and IT decision-makers are in a race to achieve interoperability between diverse identity...

Cybersecurity is non-negotiable. So, when it comes to enterprise budgets, it’s the one place we typically don’t see cuts — even in an unpredictable economic environment....

The hardest part of identity and access management (IAM) technology is making it work with multi-vendor infrastructure and the growing number of applications that enterprises rely...
