Hackathon: authenticating header-based apps

The team at Strata loves nothing better than a challenge. After all, the company was founded on the philosophy of making the impossible possible. So, like everyone else here, I was completely on board when our engineering, product, and design (EPD) group suggested a hackathon.
I really wanted to use the hackathon as an opportunity to create an approachable project that would showcase key features and functionalities of the identity fabric that our team has spent the last few years defining and refining.
Creative thinking to solve the big, gnarly IAM problems
Our customers often come to us with huge identity and access management challenges that no other vendor has been able to solve. These challenges can be gnarly, but because our EPD has the experience, creativity, and background to see how to solve big, bad IAM problems, even the worst ones are usually “just another day at the office.” However, we’ve often seen problems that require extra creative thinking because the functionality was not inherently part of the product — yet!
Defining the problem
The core problem our enterprise customers face can be summarized in three parts:
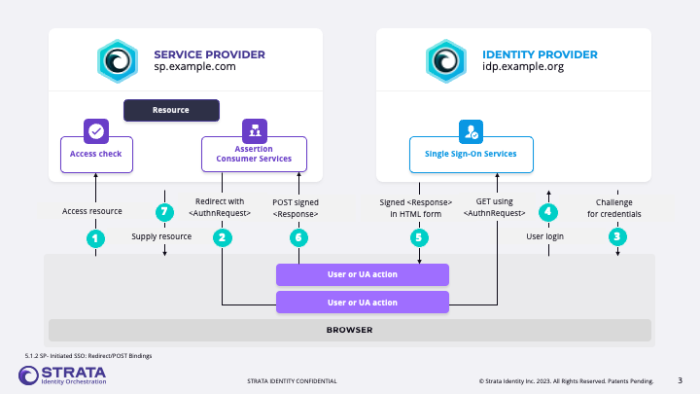
- Our users must authenticate to our systems using single sign-on (SSO) backed by modern protocols and technologies like SAML, OIDC, and MFA.
- However, our internal ecosystem contains fleets of bespoke applications that do not know or understand those protocols.
- We need to expediently bridge this gap without breaking the bank.
Taking that problem into account, we defined a project that would:
- Showcase and solve this use case using a single orchestrator.
- Ensure the project can be described, demoed, and showcased in 3 minutes or less.
- Keep the interaction short but engaging for the end user.
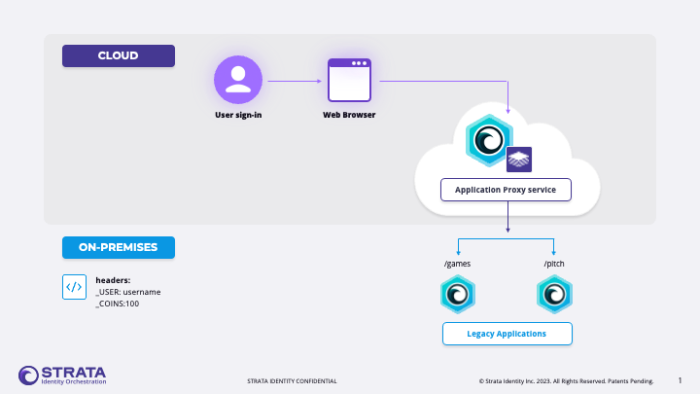
The legacy app we chose to emulate used header-based authentication. The practice of header-based apps was established many years ago, and due to all the realities of running and maintaining technical systems, many of these applications remain in place today at organizations. They’re old but not likely to go away any time soon.
Let’s go! Putting our ideas into action
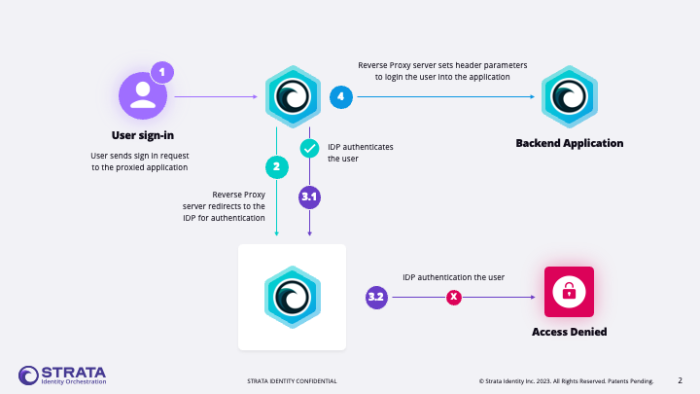
With all of the above context in mind, my hackathon partner and I ensured the work we were taking on was appropriately sized, and in less than a day of work, we were able to use a single instance of Maverics in five unique ways:
- Host a localhost website (facsimile of legacy header-based app)
- Act as a SAML identity provider (SAML IDP)
- Act as a proxy gateway to access the localhost site from the internet
- Restrict certain pages to authenticated users
- Provide a modified user experience (UX) based on that authentication
The project: Orchestration of ephemeral tomfoolery
ephemeral: something that lasts for a very short time: something ephemeral
tomfoolery: playful or foolish behavior
arcade: an amusement center having coin-operated games
Project concept
Goal: To create a fun atmosphere that draws attention and encourages engagement.
The site will serve “coin” operated games/novelties/experiences. Overall, we desire to build a fun and engaging client that highlights the harmony, customizability, and innovativeness of Strata’s available technologies.
Project results
At the end of the hackathon, we had built an interactive site with a simple game:
- In this project, we solely used the orchestrator to serve content, authenticate, and authorize sites/areas on https://ephemeral.fun.
- Users log in with a custom user ID and start with a set amount of coins upon initial login.
- From there, they can spend them on short game sessions/sites within the site or trade them with other active players.
- The coin-operated game could be anything technically; it is a redirect and unique session with limited time that eventually redirects you back to your previous location and session.
- We make use of service extensions to serve and protect content in innovative ways.
Watch a brief demo.
A hackathon in retrospective
During the last two years working at Strata, I have learned a lot about identity and access management (IAM) practices used by the modern enterprise. Along that journey, we have solved some very interesting and challenging problems previously considered unsolvable. This experience has helped me stay curious at all times, which often leads to the most creative solutions.
The hackathon project was a hands-on way to do just that. It was fun to use our identity fabric in such a multifaceted and innovative way. Also, this marked the first time I had personally gotten a public website online, accessible via HTTPS. It was rewarding to see the telemetry data being generated live during the demo as people were using it. Creating something myself using the orchestrator technology we always provide for others was a great perspective and overall fulfilling project.
Modernize any app with any IDP in minutes. Join the 'Orchestration Kitchen' workshops.