Identity & Access Management
State of Multi-Cloud Identity Report 2022
Executive summary
Enterprises have accelerated their move to multiple cloud platforms over the past 12 months and intend to keep pushing in this direction. An increasing share of app workloads are hosted across multiple cloud platforms, but with only a minority of enterprises planning on giving up on-premises approaches entirely, most enterprises face the combination of hybrid and multi-cloud in perpetuity.
Successfully achieving the promise of a combined hybrid and multi-cloud future can only be gained if enterprises address their technical debt and outdated IAM (identity and access management) practices. Distributed identities across scattered identity silos result in inconsistent identity and access policies when people are accessing apps. Poor visibility of existing access policies means enterprises are flying blind—they do not know where apps are hosted, nor who has access to their data.
Current identity standards and technologies for multi-cloud policy management are failing to live up to the actual demands of multi-cloud, and enterprises are having to hire expensive identity architects to fill the gap. Nevertheless, data breaches continue, the identity threat looms large, and more strategic identity and IT modernization initiatives remain unaddressed.
Modernizing identity and access management is a strategic imperative for enterprises with hybrid and multi-cloud strategies. Consistent policies irrespective of where app workloads are deployed are essential; relying on identity architects to manually stitch these together is not a sustainable approach. A new category of software—Identity Orchestration—offers a better solution: a distributed abstraction layer that integrates multi-cloud and hybrid identity infrastructures and allows fine-grained enforcement of consistent identity and access policies. Identity Orchestration supports security modernization through Zero Trust approaches, and also gives enterprises the ability to achieve consistent Policy Orchestration between cloud platforms and across the tech stack.
What you will learn from this report
- The top identity challenges facing organizations using multiple cloud platforms.
- The costs to compliance, security, and modernization of uncoordinated identities, visibility gaps, and reliance on unsustainable approaches to identity and access management.
- Insights to guide your organization’s business decision-making processes, technology selection, and strategies to support digital transformation.
About this report
Osterman Research conducted a survey for this research and prepared this report under commission from Strata Identity. Information about Strata Identity is provided at the end of the report.
We encourage the reuse of data, charts, and text published in this report under the terms of this Creative Commons Attribution 4.0 International License. You are free to share and make commercial use of this work as long as you attribute the Strata 2022 State of Multi-Cloud Identity Report as stipulated in the terms of the license.
Key findings
2022 is the year of multi-cloud acceleration
Enterprises have accelerated their adoption of multi-cloud over the past year. The two leading drivers were:
- Achieving redundancy and high availability.
- Increasing IT modernization.
Enterprises continue to migrate an increasing share of apps to the cloud, but even with planned modernization over the next 12 months, achieving the perfect target state of apps in the cloud remains limited by reality. For example, more enterprises are having to manage global access for data in cloud systems, and geo-segmenting access to data is a growing concern.
Legacy tech debt and outdated IAM practices weigh down multi-cloud adoption
Enterprises are struggling to ensure consistent user identities as they adapt to life in the cloud. Identity is already scattered across multiple systems. Modernizing to the cloud compounds the challenge.
We found that:
- Visibility of app hosting and access policies are ‘cloudy’ for enterprises using multi-cloud.
- Current identity standards and technologies for multi-cloud policy management are strained by the demands of multi-cloud.
Organizations are modernizing identity for multi-cloud
The modern multi-cloud world demands consistency in identity and access policies across cloud platforms and the stack. Deploying multi-factor authentication and modernizing identity for multi-cloud are strategic initiatives for most enterprises, in combination with a range of initiatives that support a zero trust approach.
Identity Orchestration to achieve zero trust
While identity challenges hinder the move to multi-cloud, Identity Orchestration offers the missing answer for integrating multi-cloud and hybrid identity infrastructures. One core component of Identity Orchestration is Policy Orchestration, where access policies are managed in a coordinated and unified manner across multiple cloud platforms. This ensures users are always and only ever granted a consistent set of access rights irrespective of the cloud platform used by the enterprise or the resource being accessed by the individual. Policy Orchestration is an integral part of the journey to modern multi-cloud identity.
The year of multi-cloud acceleration
Change is everywhere. Business models have transformed to embrace recent global disruptions. Digital channels have created new opportunities for customer engagement. Multi-cloud adoption has accelerated. Enterprises with successful IAM architectures are evolving to facilitate secure operations and oversight in a world of distributed IT platforms and users. As multi-cloud strategies take hold, the increasing number of identities scattered across silos expands the difficulty of securing distributed identities with modern authentication approaches. In this section, we look at the acceleration to multi-cloud, app modernization for multi-cloud identity, and the need to manage global access to data.
Enterprises are and will continue to be multi-cloud
Virtually all enterprises have moved to cloud services (as have all the enterprises surveyed for this report), and most already use multiple clouds (a weighted average of 2.7 cloud services currently in use vs. 3.1 anticipated in 12 months). Currently, 15% of enterprises use four or more clouds; in 12 months, 37% expect to do so. Cloud services are of two major types: private and public. Private cloud services are managed by a service provider for a specific client, while public cloud services are multitenant offerings from the likes of Amazon, Microsoft, IBM, and Google. See Figure 1.
Figure 1
Number of Clouds in Use: Current and Forecast
Percentage of respondents

Source: Osterman Research (2022)
Larger enterprises already use more clouds than smaller enterprises and intend to keep it that way: 82% of enterprises with $1B+ in revenue currently use three or more clouds, up from 66% last year. Among smaller enterprises, 49% currently use three or more clouds. In 12 months, three or more clouds are expected to be used by 95% of large enterprises and 58% of smaller ones. Multi-cloud adoption is driven by organizational strategy and merger-and-acquisition activity and is frequently a byproduct of departmental managers and remote employees spinning up cloud services to support productivity and collaboration needs.
Many roads lead to multi-cloud
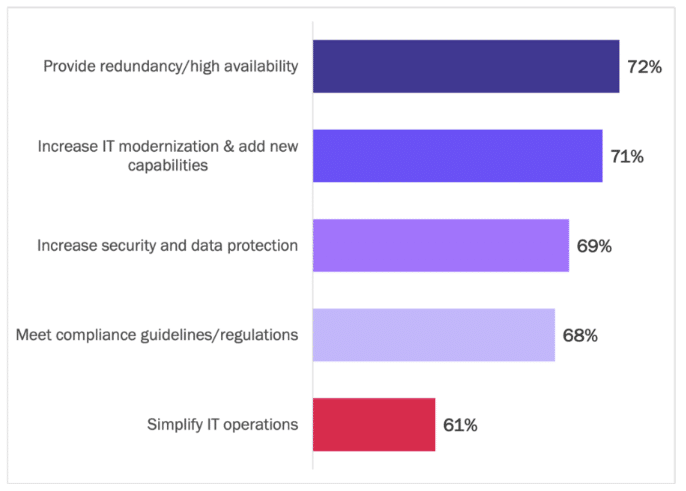
The most important driver for enterprises adopting multi-cloud is providing redundancy and high availability, followed by IT modernization. Improving security and data protection as well as satisfying regulatory compliance obligations feature highly. See Figure 2.
Figure 2
Top Five Reasons for Accelerating Multi-Cloud Adoption
Percentage of respondents indicating “important” or “extremely important”
Source: Osterman Research (2022)
Providing redundancy was a lower-rated reason for adopting multi-cloud in last year’s survey. Its ascendancy to first place this year is in line with the growing centrality of cloud services in digital transformation initiatives, including supporting a hybrid workforce and creating new digital channels to engage with customers. Downtime kills hybrid workforce productivity and threatens global customer engagement, and high-profile outages at major cloud platforms have underscored the need for multi-cloud strategies to assure availability and resilience. Security and data protection are top-of-mind issues due to growing cyber threats and multiple high-profile data breaches where identity compromise and theft have been leading causal factors.
The path to the cloud is busier than ever
Enterprises are moving an increasing share of their apps to the cloud. Half of enterprises currently host over 60% of their apps in the cloud, and four out of five expect to do so in 12 months. Last year, only one-third of enterprises said that more than 50% of their workloads were in the cloud, meaning two-thirds of enterprises still had the majority of their app workloads on-premises. Most enterprises are over halfway through their app workload modernization. See Figure 3.
Figure 3
Percentage of Apps in the Cloud: Current and Forecast
Percentage of respondents
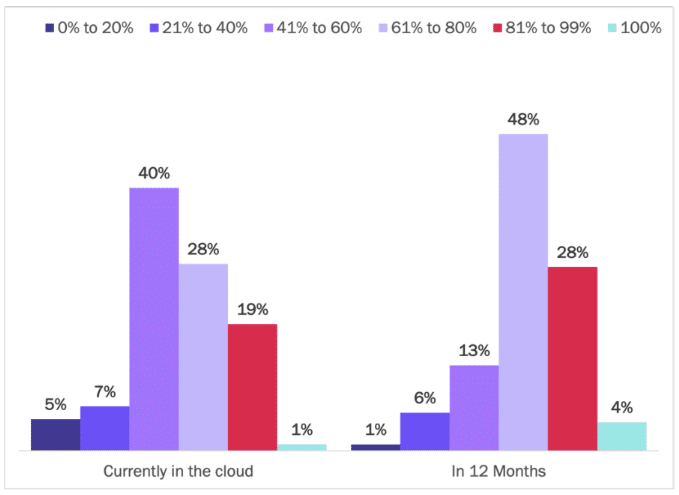
Source: Osterman Research (2022)
But reality still limits cloud aspirations
While one-third of enterprises expect to have 80% or more of their apps in the cloud within 12 months, almost two-thirds of enterprises see that as their perfect target state.
Currently, only one-fifth of enterprises have achieved this level of modernization, and although another one in two will reach it within 12 months—that is still only half of those enterprises that want to achieve this target state.
Only 20% of organizations think they will be able to move away from on-premises applications entirely, which means most will need to manage identity and policy across on-premises apps and multi-cloud apps indefinitely.
See Figure 4.
Figure 4
Percentage of Apps in the Cloud: Perfect Target State
Percentage of respondents
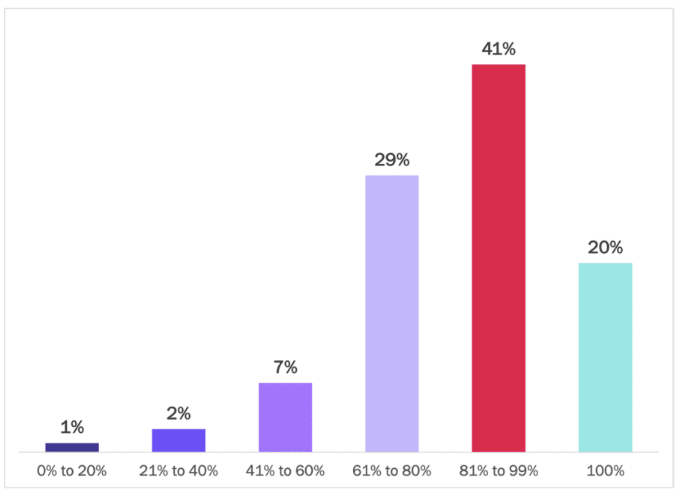
Source: Osterman Research (2022)
Global considerations for global data
As enterprises have adopted multi-cloud strategies and are migrating an increasing share of apps to cloud platforms, they face a diverse, evolving, and accelerating regulatory landscape, e.g., GDPR (General Data Protection Regulation), CCPA/CPRA (California Consumer Privacy Act and California Privacy Rights Act) and other state-level data privacy regulations in the United States, and PIPEDA (Personal Information Protection and Electronic Documents Act). The need to manage global access to data is a current reality for 88% of organizations, up from 76% in our 2021 survey. See Figure 5.
Figure 5
Importance of Managing Global Access for Data in Cloud Systems
Percentage of respondents
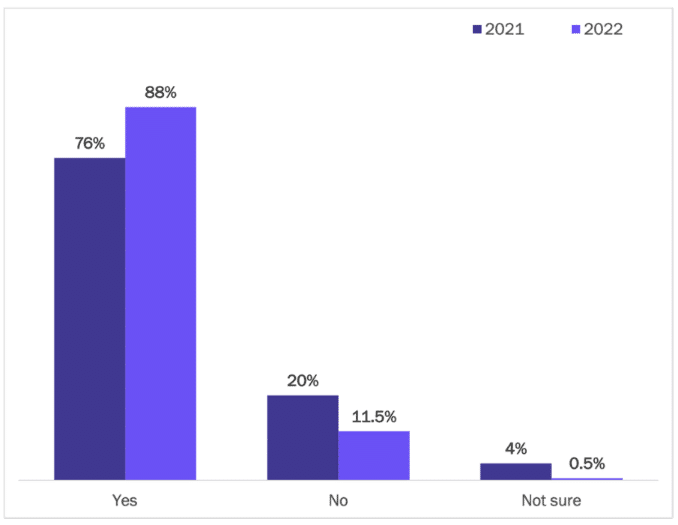
Source: Osterman Research (2022)
In parallel with this growth in managing global access for data is the high proportion of enterprises that must segment access policies by geography to deliver on regulatory mandates. Geo-segmentation of access policies is a current reality for 68% of enterprises. Instead of having a single and unified access policy that applies irrespective of where app workloads are deployed, geo-segmentation splinters access policies along geographical deployment lines in multi-cloud scenarios.
Legacy tech debt and outdated IAM practices weigh down multi-cloud adoption
The identity of employees and customers is the fundamental building block for providing secure access to data and applications. Enterprises are struggling to ensure consistent user identities as they adapt to life in the cloud. In this section, we look at the hindrances to multi-cloud identity.
The cloud journey faces challenges, new and old
Concerns with data privacy (77% of respondents indicated this is a significant or extremely significant barrier) and the challenges of managing identities across multiple clouds (66%) are the two top-ranked barriers preventing organizations from achieving their desired perfect target state of apps deployed in the cloud. Inconsistent identities across cloud services fuel the threat landscape, including overprovisioned access rights and data breaches. See Figure 6.
Figure 6
Barriers Preventing Organizations from Achieving Their Target State of App
Workloads in the Cloud
Percentage of respondents indicating “significant” or “extremely significant”
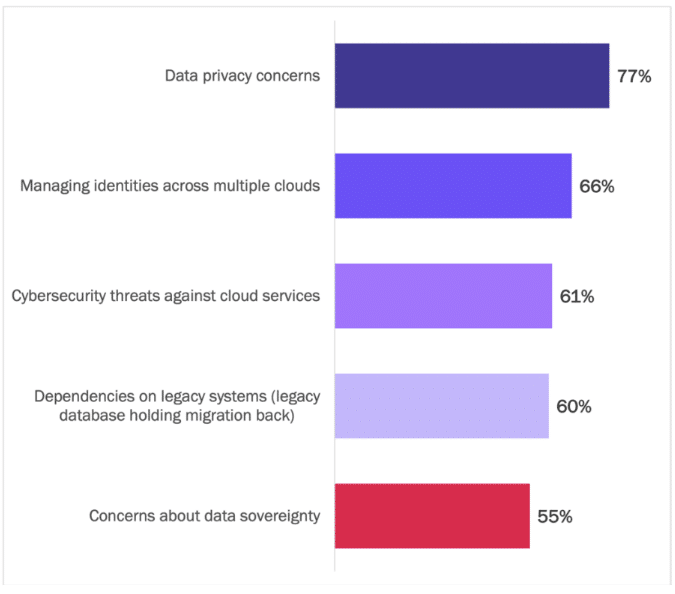
Source: Osterman Research (2022)
Distributed identities are more scattered than ever
Enterprises are managing employee identities across a scattered collection of identity systems. The two most common systems are AWS Cognito (at 27% of enterprises) and Microsoft Azure AD (25%). Another 16% of enterprises make use of Microsoft Active Directory, Microsoft’s on-premises identity offering. A range of other identity systems are in use, covering both cloud-specific identity systems and single sign-on offerings. See Figure 7.
Figure 7
Systems Used to Manage Workforce Identity
Percentage of respondents
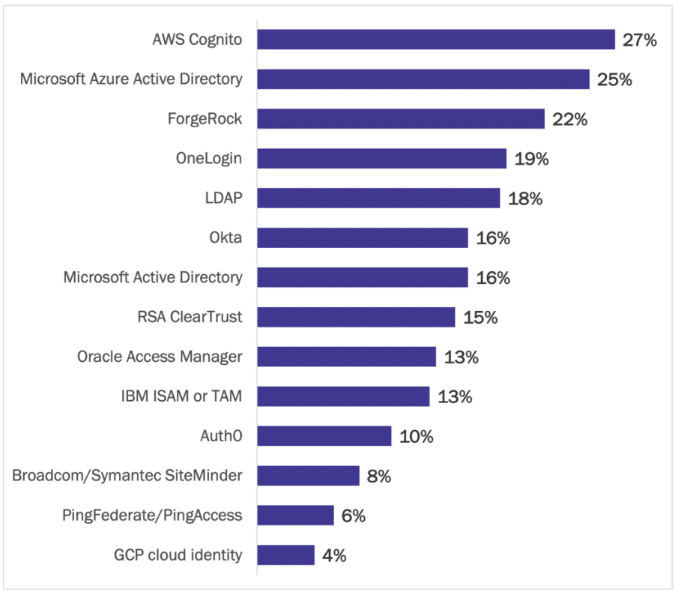
Source: Osterman Research (2022)
Most enterprises are already managing identity across multiple systems:
- 70% of enterprises use two or more identity systems
Most enterprises use two or more identity systems for employees: 47% use two, 16% use three, and 7% use four or more. Only 30% of respondents say their enterprise uses a single system to manage workforce identity. - Microsoft is more frequently used at larger enterprises (with over $1 billion in revenue)
Larger enterprises are more likely to use Microsoft Azure AD (42%) and Microsoft Active Directory (30%) than smaller enterprises (18% for Azure AD and 11% for Active Directory). Larger enterprises also make greater use of AWS Cognito (32% vs. 25% at smaller enterprises).
Managing multiple clouds with distributed identities is no easy task
Enterprises face a range of challenges with managing the identities of users across multiple cloud platforms and identity systems. The most significant challenges revolve around managing different user types, the lack of automated tools for managing identities, and the incompatibilities of legacy systems with cloud platforms. See Figure 8.
Figure 8
Challenges with Managing Identities and Apps Across Multiple Clouds
Percentage of respondents indicating “agree” or “strongly agree”
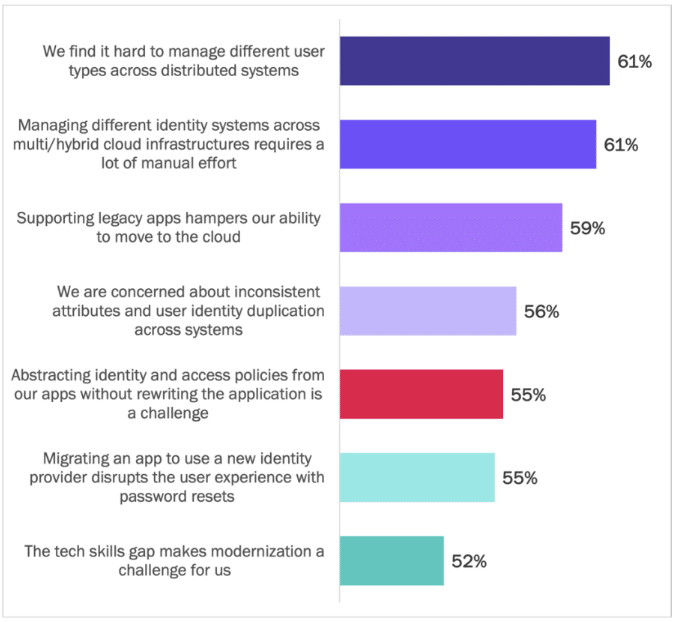
Source: Osterman Research (2022)
In addition, respondents indicated a lack of effective capabilities to handle the following aspects of migrating to the cloud or adopting cloud services:
- Weak processes for automated revocation of access
49% of enterprises were not confident that removing a user from their identity system would immediately revoke their access to all corporate apps and data, whether hosted on-premises or in the cloud. - Difficulty in accessing source code for apps
43% of enterprises indicated they would struggle to locate the source code for all their apps, thus hindering identity and app modernization activities. Legacy apps from vendors no longer in business, tech debt, and app creators who have long gone all contribute to this difficulty.
Problems arise when multiple platforms ‘cloud’ visibility of policies
Using multiple clouds enables enterprises to reap redundancy, availability, and modernization benefits, but enterprises are losing track of where their apps are hosted across a multi-cloud deployment. This increases the likelihood of data breaches, overprovisioned access, and unauthorized data exposures.
Visibility gaps are a significant problem for three out of five enterprises. For two out of five enterprises, distributed identity systems across multiple clouds have decreased visibility into access policies. See Figure 9.
Figure 9
Challenges in Cloud-Hosted Apps: Visibility Gaps in Access Policies
Percentage of respondents indicating it as a “problem” or “extreme problem”
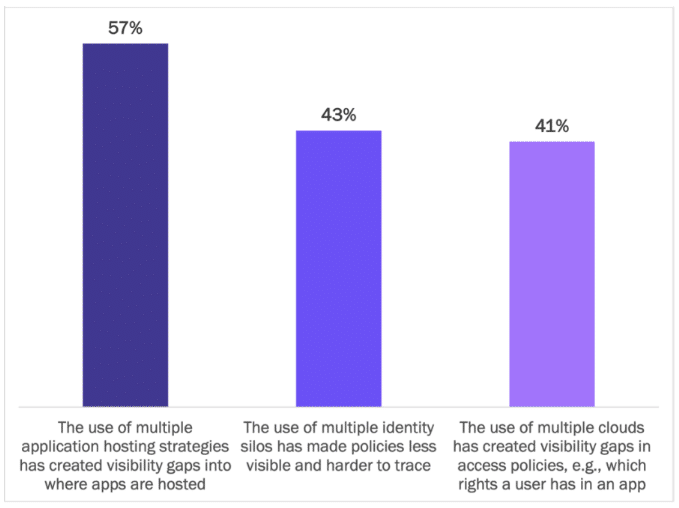
Source: Osterman Research (2022)
‘Clouded’ visibility of policies creates more work and uncertainty
As enterprises embrace a multi-cloud future, the need to discover existing access policies per app and across all the cloud platforms becomes essential. However, only 25% of enterprises have the tools to discover all existing access policies easily.
The remaining enterprises require manual work to discover and map existing access policies (47%) or can discover only a partial set (27%). There are a range of reasons for this, such as:
- The departure of app owners who did not transition ownership to a new app owner before leaving.
- Apps on legacy cloud platforms that have not been fully decommissioned.
- Unintentional cloud adoption where a single department starts using a new cloud platform without informing the IT operations team.
- App deployments that are driven by urgent requirements that bypass normal approval channels.
Incomplete and manual approaches make the deployment and ongoing management of identity and access policies much more difficult. Policy management is not done properly, which creates security gaps that raise the likelihood of data breaches, poor credential hygiene, and inappropriate access to corporate data. See Figure 10.
Figure 10
Discovery of Access Policies in Multi-Cloud
Percentage of respondents
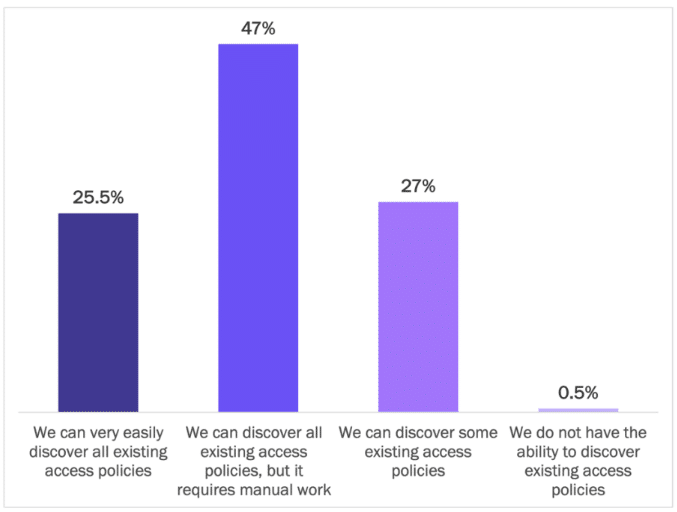
Source: Osterman Research (2022)
Current identity standards are limited
Current identity and access management standards only partially solve the challenges with multi-cloud identity. Enterprises indicate that their full requirements are unsupported by these standards. Current standards have reached their working limits because they were not built to support the specific needs of multi-cloud identity. This is particularly true of NTLM and LDAP, which offer the least support for multi-cloud identity. See Figure 11.
Figure 11
Current Standards Do Not Solve Multi-Cloud Identity Management Challenges
Percentage of respondents indicating incomplete support of requirements
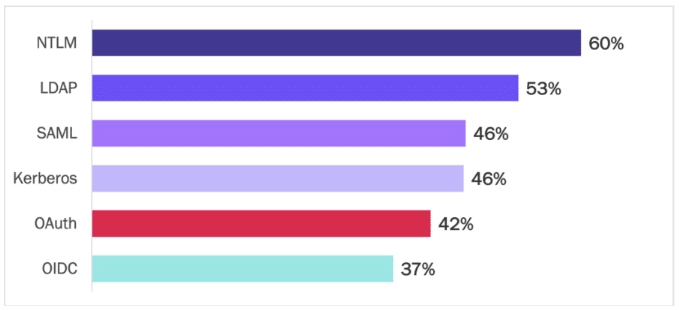
Source: Osterman Research (2022)
Technologies for multi-cloud policy management come up short too
A similar experience is reported with current identity and access management technologies for distributed multi-cloud and hybrid cloud policy management. Current approaches provide but partial coverage of requirements, creating gaps in visibility, control, and security. Apache Ranger, OPA, and IdentityIQ are viewed as offering the least support for multi-cloud policy management. See Figure 12.
Figure 12
Current Approaches to Policy Management Are Not Enough
Percentage of respondents indicating incomplete support of requirements
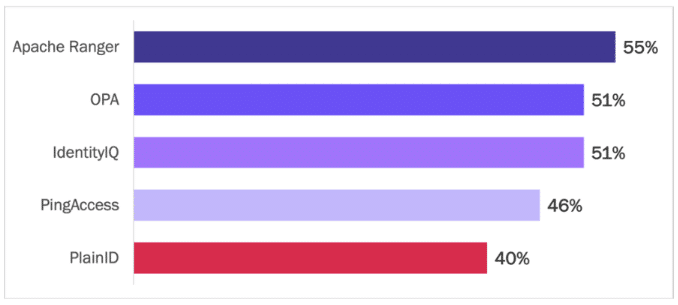
Source: Osterman Research (2022)
Hiring for multi-cloud identity is one way to fill this gap
To address the technology gaps created by these competing platform-specific identity systems, organizations are hiring additional technical staff or extending current duties to include managing identity and access management policies across cloud platforms. The three leading approaches are hiring semi-specialists (40% of respondents), generalists (29%), and specialists (26%). See Figure 13.
Figure 13
Approaches to Managing Identity and Access Policies
Percentage of respondents
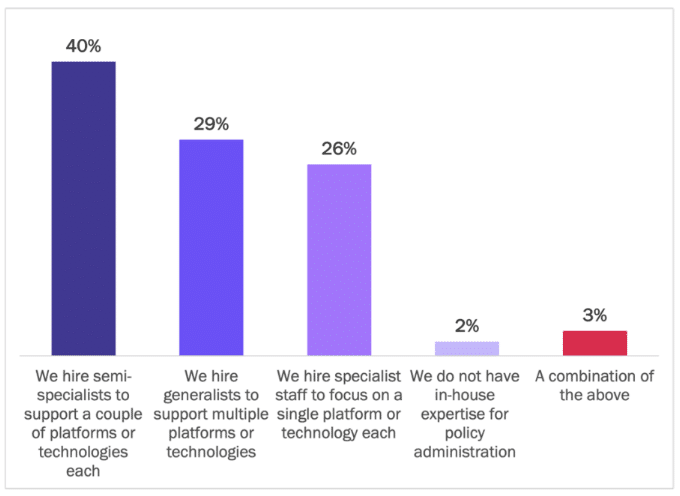
Source: Osterman Research (2022)
Manual efforts to manage, administer, and maintain consistent identity and access policies across multiple clouds is an expensive proposition that inflicts opportunity costs on organizations. Salaries invested in identity management engineer and architect roles (at $140,000 to $180,000 in annual salary plus benefits per role in the United States) cannot be invested in more strategic initiatives and driving innovation. Enterprises are stuck on hiring identity specialists as the way to orchestrate adaptive access policies across their on-premises infrastructure and a growing array of multi-cloud services.
Why respondents are losing sleep over multi-cloud identity
We asked respondents to describe their enterprises’ most significant identity management challenges. Across the over 200 respondents, four key themes surfaced most frequently:
- Governing access policies
Respondents said they were challenged with “knowing who has access to what,” “identifying employees’ authority, responsibilities, and deliverables,” and being able to provide “access to the tools and information [their] employees need while also keeping [their] data secure.” One respondent said they wanted “full control of who has access to applications and data, where they are accessing it, and what they are doing with it.” Another felt they were negatively impacted when “excessive permissions [are] granted to users with no business need.” - Identity security challenges
Respondents took issue with employees using weak passwords and insecure approaches to authentication. Specific challenges included “password fatigue causing employees to use obvious and insecure passwords,” “risks presented by password reuse and using online notes to remember passwords,” and the challenge of “[moving] from passwords to potentially less vulnerable systems.” One respondent commented that “usernames and passwords are not always the most secure way to control account and resource access,” particularly across “multiple domains” and “multiple applications.” - Matters of cost and/or budget for identity management
Respondents noted a wide selection of challenges related to cost and/or budgeting. One challenge was focused on multi-cloud, such as “determining the costs of applications and services,” “reducing costs while retaining control of infrastructure,” and “optimizing SaaS subscription expenses.” Another challenge was around implementation and modernization costs, e.g., “cost of implementation,” “It takes time and is expensive to integrate with some apps,” and “expensive integration ends up creating problems in the area.” - Deprovisioning access when employees leave or change roles
Ensuring rapid, complete, and accurate removal of access rights when employees are terminated, leave the enterprise, or change to a new role is the fourth area of high concern. Respondents found it challenging to “revoke all access [when an employee is terminated],” to handle the removal of access “when employees or business partners are no longer with [the company] or engaged on a project,” and to deal with “role changes.” The threat of insufficient capabilities is that “critical business applications and data are in the hands of potentially disgruntled former employees if [the] de-provisioning process is not done correctly.” One respondent said they rely on “manual user deprovisioning across all applications” (which is error-prone and expensive). Another commented that their “IT team is not doing a good job of off-boarding employees which has caused a lot of issues.”
Identity modernization for today’s multi-cloud world
The adoption of multi-cloud for app deployment has highlighted challenges with current identity and access management approaches. In this section, we look at how enterprises are modernizing identity for their growing multi-cloud environment.
Consistent policies are equally important between clouds and across the stack
The importance of ensuring consistency in identity and access policies leaps as enterprises adopt a multi-cloud and hybrid approach. The data shows that the importance of consistent policies across multiple cloud platforms is almost six times higher at enterprises using two or more clouds versus those relying on a single cloud-only (77% versus 13%). The importance of consistency across the stack is seven times higher with multi-cloud than a single cloud (78% versus 11%). See Figure 14.
Figure 14
Importance of Consistency in Identity and Access Policies
Percentage of respondents indicating “important” or “extremely important”
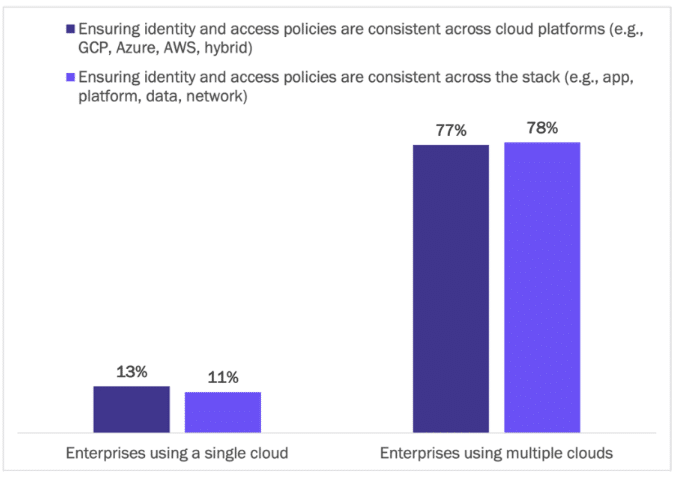
Source: Osterman Research (2022)
Enterprises relying on a single cloud may agree with the importance of consistency in theory, but as soon as an enterprise adopts multi-cloud—or finds itself with multiple clouds due to merger and acquisition activity or departmental adoption—consistency becomes a core mandate. However, even enterprises using a single cloud realize that they need to think about their strategies for multi-cloud identity.
Out with the old and in with the new
Enterprises are investing in a range of initiatives to modernize their identity infrastructure to support multi-cloud approaches. Deploying modern authentication capabilities, such as multi-factor authentication (MFA) ranks as the highest strategic priority (74%), followed by identity infrastructure modernization (67%) and continued migration of apps to the cloud (66%). See Figure 15.
Figure 15
Strategic Importance of Identity Initiatives
Percentage of respondents indicating “important” or “extremely important”
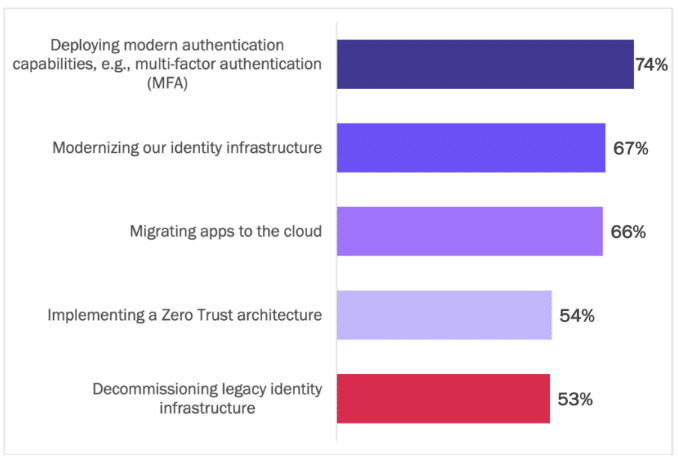
Source: Osterman Research (2022)
Enterprises are securing an average of 55% of apps with MFA irrespective of app type and deployment location:
- SaaS apps offered by cloud providers (e.g., Salesforce, Workday): 56%
- Commercial off-the-shelf/custom apps deployed on public clouds: 55%
- Commercial off-the-shelf/custom apps deployed on private clouds: 54%
- Commercial off-the-shelf/custom apps deployed on-premises: 53%
Only one in five enterprises have already secured 80% or more of their app landscape by MFA.
Implementing a zero trust architecture is ranked as the fourth most important initiative. Zero trust can be interpreted as a broader term encompassing a variety of initiatives—such as the top-ranked modern authentication strategy—rather than an individual solution to deploy. Another way of saying this is that zero trust is a mindset that requires an overall change in how an enterprise approaches security.
Driving security modernization with zero trust
Embracing a zero trust architecture is driving a set of initiatives by enterprises, with three very closely ranked initiatives topping the list:
- Classifying and protecting data per user type, for example, to meet data protection mandates.
- Driving consistency in identity and access policies for partners and vendors, for example, to minimize data breaches and third-party data risks.
- Ensuring tight control for privileged user accounts, for example, to minimize insider threats or devastating consequences after an administrator’s account is compromised.
See Figure 16.
Figure 16
Priorities in Adopting a zero trust architecture
Percentage of respondents indicating “important” or “extremely important”
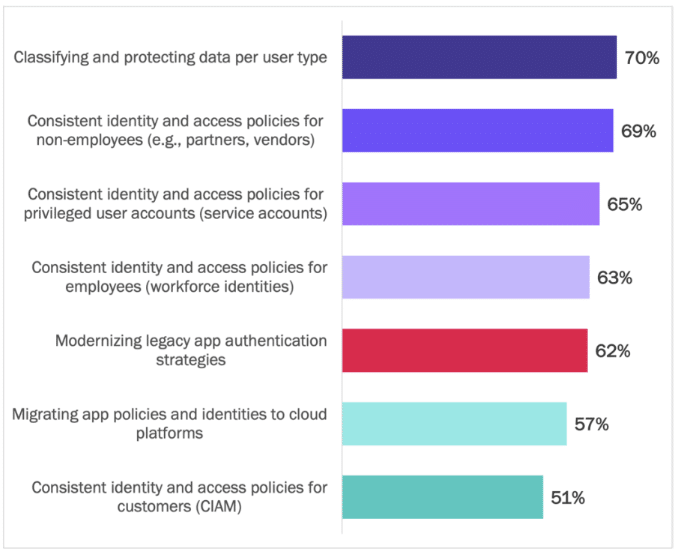
Source: Osterman Research (2022)
All seven of the priorities listed in Figure 16 are ranked as “important” or “extremely important” by more than half of the respondents. That is a lot to deliver on. Successfully implementing each initiative while also factoring in the interaction between each initiative requires specialist know-how, the availability of skilled professionals, and a clear roadmap on how to start. Many enterprises will struggle to meet these demands as they also navigate geopolitical challenges, uncertain hybrid workforce dynamics, and post-COVID malaise.
Policy Orchestration is achieved through Identity Orchestration
Enterprises are facing the consequences of multi-cloud approaches, even while they accelerate the movement of app workloads to cloud platforms and modernize IT to drive flexibility and innovation. Enterprises have found the road to the cloud full of identity challenges, including:
- Data privacy
How to meet an inconsistent collection of data privacy and data protection mandates when apps are hosted on global platforms and accessed from many geographies. - Zero trust
How to enact the zero trust principle of only giving the right level of access to the right person under the right conditions when identities are scattered across disparate identity silos and access policies can only be maintained with ongoing manual reconciliation efforts. IAM is the bedrock of zero trust, but many enterprises find their IAM approaches unstable and crumbling. - Partial visibility
How to ensure visibility of changing hosting regimes for app workloads and enforce consistent access policies. Most enterprises are operating with partial visibility and uncoordinated policies. This creates an environment ripe for data breaches. Loss of customer trust is a swift consequence of data breaches, along with declining corporate value and actions by regulators to impose regulatory fines.
To cope with these identity challenges, enterprises are hiring identity architects and engineers to manually create and maintain consistent identities and access policies across multi-cloud deployments. This approach comes with high costs—in the short-term in the form of high salaries, but more critically, in long-term opportunity costs due to the side-lining of more strategic identity and IT modernization initiatives.
Identity Orchestration offers a better approach. Identity Orchestration is a distributed abstraction layer that integrates multi-cloud and hybrid identity infrastructure and allows fine-grained enforcement of consistent identity and access policies. This section looks at how Identity Orchestration enables enterprises to achieve Policy Orchestration.
Policy Orchestration addresses inconsistent access policies in multi-cloud
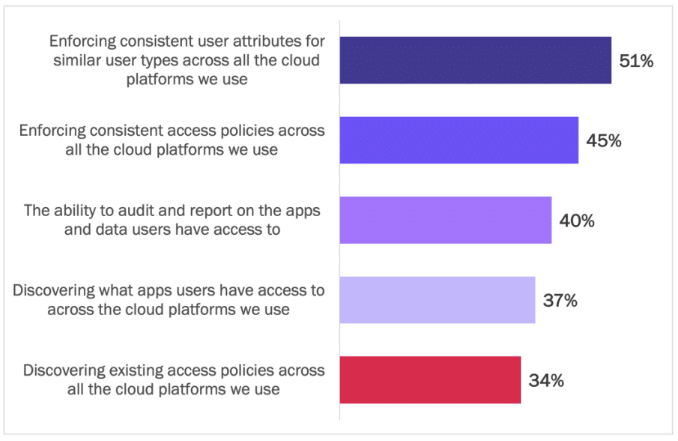
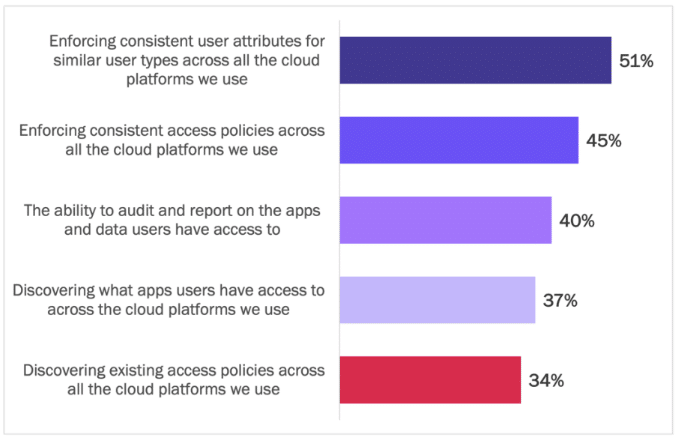
Many respondents indicated their current capabilities are ineffective for orchestrating policies across multi-cloud deployments. Multiple challenges exist:
- User attributes are inconsistent across multiple cloud platforms.
- Access policies are out of sync across multiple cloud platforms.
- Auditing and reporting on apps and data to which users have access is incomplete and unreliable.
- Methods of discovering apps and access policies offer only partial visibility.
Enterprises risk data breaches, data leakage, regulatory fines, and loss of customer trust when inconsistent access policies undermine the intent of zero trust architectures, giving threat actors and malicious insiders alike access to apps and data they should not have. See Figure 17.
Figure 17
Challenges Faced Managing Identity and Access Policies in Multi-Cloud
Percentage of respondents indicating capabilities are not effective
Source: Osterman Research (2022)
Many enterprises still rely on manual efforts to address these challenges, as well as attempting to drive consistency in multi-cloud environments. This is why Identity Orchestration software offers a better way of achieving multi-cloud Policy Orchestration. It solves the challenges of distributed identity in multi-cloud and hybrid environments by leveraging an abstraction layer to coordinate siloed identity systems, allowing them to work as one. IT and security teams can create seamless and secure identity experiences across their complex environments, as well as modernizing legacy applications without rewriting application code. The Identity Orchestration approach increases security and compliance by ensuring consistent access policies wherever apps are deployed, frees identity professionals from repetitive manual integration activities, and creates the opportunity for greater investment in the strategic identity modernization agenda.
Policy Orchestration drives the Identity Orchestration imperative
Policy Orchestration is where access policies are managed in a coordinated and unified manner across multiple cloud platforms. Users are always and only ever granted a consistent set of access rights irrespective of the cloud platform used by the enterprise or the resource being accessed by the individual.
The consistency enforced by Policy Orchestration eliminates variability in access policies that could previously be misused to gain unauthorized access to data. Policy Orchestration is a fundamental step in distributed enterprise security because it works across different cloud platforms and deep into the stack to unify policy management.
Policy Orchestration is facilitated by Identity Orchestration which decouples identities from the identity system via an abstraction layer called an identity fabric—a distributed identity management framework that discovers, abstracts, integrates, and orchestrates identity data consistently across hybrid and multi-cloud platforms. Policy Orchestration is an integral part of the journey to Zero Trust security via Identity Orchestration.
Enterprises highly value a set of outcomes in the multi-cloud journey:
- Future-proofing identity architecture (68% of respondents say this is important or extremely important to their organization).
- Removing dependencies between apps and specific identity providers (67%)— which creates the fluidity required for modernizing apps, decommissioning legacy identity silos, and quickly responding to future changes in identity systems.
- Enforcing consistent runtime access policies for apps across multiple clouds (63%)—so no one gets varying access rights depending on what cloud platform is hosting a given app.
Each of these is of significant strategic value to enterprises as they accelerate their adoption of multi-cloud strategies and move an increasing share of apps to cloud platforms. See Figure 18.
Figure 18
What Enterprises Want from Identity Orchestration
Percentage of respondents indicating “important” or “extremely important”
Source: Osterman Research (2022)
Conclusion
Enterprises struggling to guarantee consistency in identity and access policies for app workloads deployed across various multi-cloud platforms risk data breaches driven by identity failures. Few enterprises can orchestrate identity and access policies without relying on manual refactoring efforts, and even then, having to put up with only limited visibility and weak identity controls.
Identity Orchestration software offers the missing answer to the challenge of fluidly orchestrating policies across multi-cloud platforms — driving seamless consistency in access and identity policies, freeing identity professionals to invest in strategic Zero Trust initiatives and moving toward a distributed Identity Orchestration
framework.