Why SSO is only part of multi-cloud identity

Over the past few decades, single sign-on (SSO) has become the default security solution for most companies. It’s convenient for users, so they actually use it. SSO also improves organizational security by keeping the number of accounts and passwords low.
SSO came on the scene as companies struggled to manage multiple applications’ identities. Each app had its own authentication system, user IDs, and passwords. That created duplicated work for IT administrators and headaches for end-users.
Single sign-on is also a great way to roll out advanced identity capabilities like multi-factor authentication (MFA) and self-service user management. Undoubtedly, it’s a critical pillar of identity management, but it’s only one part of multi-cloud identity management.
What is SSO?
Single sign-on is authentication software that lets you sign in once and get in everywhere. It’s like having the code to unlock the outer door of a building, and all the doors inside are open for you to enter. No key or code is needed.
SSO lets you log in one time with one set of credentials. Once in, you won’t be asked to log in again to access other applications with the same organization and risk level.
There are two primary objectives of SSO:
- To make the authentication process easier for users.
- To ease the burden of managing authentication for IT teams.
There are different types of single sign-on and even more choices of an SSO software vendor. Some broad categories include:
- Federated SSO (standards-based) — enables third parties to access secured passwords so that a user only has to log in once. The most common category.
- Web access management SSO (Monolithic) — sits between the user and the application.
- Enterprise SSO — used in the workplace, allows companies to save employee time and effort. Workers sign in once and gain access to every application they’re approved to use.
- Cross-domain SSO — authenticates different application domains using the same session without reauthenticating.
No matter what type you use, SSO always operates on a specific set of principles.
How does single sign-on work?
Single sign-on software is based on a trust relationship. You only need one set of sign-in credentials, usually a username and password. Those credentials give you access to all your accounts and applications because the authentication is trusted.
That’s because SSO is a part of an infrastructure called a federated identity management system — or identity federation. Identity federation sits between the user and the account and provides access tokens that ask users to verify their identity.
Security Assertion Markup Language (SAML) is a crucial ingredient for making SSO run. The standard confirms that a user is who they say they are. SAML authenticates a user once and then communicates that authentication to multiple applications.
How is SSO implemented?
Implementing single sign-on depends on the type of single sign-on solution you choose. You also need an open standard framework called Open Authorization (OAuth). OAuth allows third-party services, like social media accounts, to connect with users’ account credentials. But OAuth keeps passwords from being exposed.
When you sign in for the first time, a cookie is created, and a central server stores the cookie. Each time you need to use the application, you’re already logged in.
What are the pros and cons of SSO?
SSO is built on trust. You enter your credentials once and gain access to many applications without having to authenticate to each one. There are clear benefits to that kind of authentication, but there are drawbacks as well.
Pros of SSO
The benefits of single sign-on include:
- Convenience. Users authenticate once to the SSO portal and then have a menu of authorized applications.
- Ease of use. Simplified authentication to multiple applications for both users and IT administrators.
- Availability. Many solutions to choose from, and implementation is straightforward and inexpensive.
- Security. SSO keeps users and organizations safer by reducing the number of access points bad cyber actors can use.
Cons of SSO
Some of the drawbacks of single sign-on include:
- Complexity. Cloud providers now work side-by-side with a company’s existing IT infrastructure, creating more complexity for identity management.
- New identity issues. As nearly every organization has become multi-cloud, new identity management challenges have surfaced. Those challenges need a multi-cloud strategy.
Is SSO a software or a solution?
Single sign-on is a framework, and it’s also software. Usually, when people talk about an SSO solution, they mean software. But not always.
Is SSO secure?
People often ask if SSO is secure. Broadly speaking, yes, SSO is secure. But some factors can affect the security effectiveness of the single sign-on process.
Multiple clouds mean new challenges for identity management
We now have multiple silos of identity vendors and multiple cloud platforms. Each cloud comes with a built-in identity system.
Is SSO secure?
People often ask if SSO is secure. Broadly speaking, yes, SSO is secure, but there are factors that can hamper the security prowess of the single sign-on process.
Multiple clouds present different challenges for identity management than in the past
We now have multiple silos of identity vendors and multiple cloud platforms. Each cloud comes with its own built-in identity system.
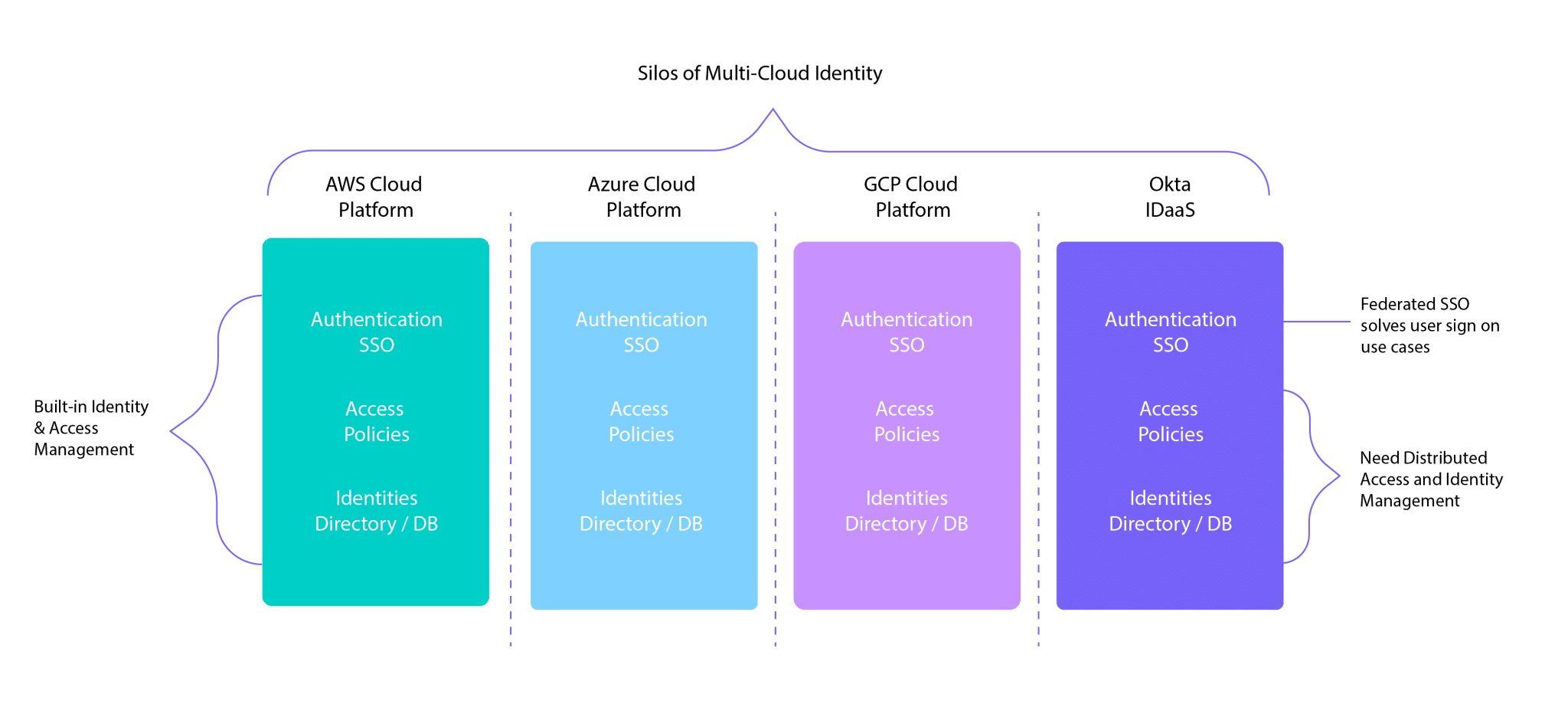
When companies adopt a cloud platform, most still use old, on-premises apps and identities. Traditional centralized identity management doesn’t work across siloed multi-cloud environments — it’s impossible to implement a consistent policy and identity.
Enterprises often need customized identity models to meet their users’ specific needs. A one-size-fits-all approach doesn’t work, and centralizing identities doesn’t let you customize.
Also, mergers and acquisitions often need highly specialized identity management capabilities during the merger integration.
These scenarios all call for identity management solutions that SSO alone can’t provide.
Technology constraints for multi-cloud identity
Enterprises often use technology platforms that become deeply entrenched in the organization, like Java or .Net, forcing developers to use one platform over another, which isn’t practical. It can also introduce delays and additional costs to software development.
Another consideration is that legacy SSO predates many of today’s standards like SAML, so many applications are locked into their current legacy SSO architecture.
Today, 75% of on-prem custom apps are integrated with SiteMinder or Oracle Access Manager (OAM). Hardcoded applications using older identity systems must be rewritten before using newer SSO identity solutions.
The need for distributed identity management
Distributed multi-cloud architectures call for distributed identity. For example, apps that work across Azure and GCP need consistent identity across both domains to give users secure access.
With so many identity silos and domains, it’s hard to know the best approach for multi-cloud identity. The use cases for multi-cloud are different from traditional SSO.
You need to manage consistent identity and access policies across platforms. Yet, today’s SSO solutions are limited to apps that are integrated with particular identity systems. Multi-cloud identity management is impossible because single sign-on only works either in the cloud or on-prem — not both.
The answer lies in extending secure access from on-prem apps to the cloud by linking on-prem identity with cloud identity. An effective solution must span across SaaS applications to on-premises applications.
The solution must also gracefully migrate on-premises apps to the cloud without rewriting or touching their code. In other words, you need to decouple an application from its old identity system and layer it onto a new identity system. And it must be transparent to your users.
The solution is distributed identity via an Identity Fabric
An Identity Fabric is a framework for managing distributed identities across multiple clouds and on-premises. An Identity Fabric orchestrates, abstracts, integrates, and discovers identity data across multiple systems (or identity domains).
The Identity Fabric orchestrates these identities and policies, then shares identity data with hybrid identity and multi-cloud infrastructures. It does this consistently and robustly.
An Identity Fabric:
- Is an abstraction layer that lets you build and run your apps on the cloud of your choice, using the identity system of your choice.
- Isn’t another identity provider (IdP) or SSO solution.
- It uses zero-code integration that avoids custom coding.
Because it provides no-code integration, the solution eliminates any need to custom code identity into apps, making it quick and easy to implement.
SSO is just one part of multi-cloud identity
SSO is an important part of your multi-cloud operation, which won’t change. But as new challenges arise, SSO alone will become less and less adequate for managing a secure cloud environment.
Enterprise companies must move quickly to stay ahead of the costly and significant challenges they’re facing. No matter how complex your cloud environment, an identity fabric can help you modernize and manage identities affordably and on your own timeline. Want to learn how to bring SSO along with you on your identity modernization journey with an identity fabric from Strata? Talk to our team of identity experts and we will show you how easy it can be.


