Legacy identity infrastructures are nearing end of life, now what?

The eventual end-of-life (EOL) is inevitable for most products. There comes a time when it simply no longer makes sense to keep investing in something.
It could be that the product is not generating enough revenue (Sony Playstation Vita), or a miscalculation was made in a diversification strategy (remember New Coke?). Or, if the company has a more significant investment in a new version or a new product, the older product will be retired, and all R&D and promotion will be put into the new one (Apple iPhones).
When it comes to EOL, software is one of the most cannibalistic product categories. New versions or next-generation technologies routinely make existing products obsolete.
What software end-of-life (EOL) looks like
Unlike packaged goods, EOL software often lives on once new releases stop and product support ends. For example, millions of older computers are still running the Windows XP operating system, but Microsoft ended support for the OS in 2014.
| Product Name | Product Version | GA Announcement | End of Life (EOL) | Type of Support |
|---|---|---|---|---|
| LegacyMinder | 12.8 | Apr1, 2018 | Mar 31, 2022 | Basic Support New features added in point releases |
| LegacyMinder | 12.7 | Jun 1, 2017 | Jun 1, 2020 | Extended Support No new features added |
| LegacyMinder | 12.6 | Aug 15, 2016 | Sept 15, 2020 | Sustaining Support Break-fix only |
The dangers of EOL for identity and access management systems (IAM)
While EOL desktop operating systems can live on adequately for years — despite posing a security threat due to a lack of new patches — identity and access management (IAM) systems are a different animal.
IAMs function as the connective tissue for enterprise IT systems. Without IAM, access to applications, data, and other resources grinds to a halt. It truly is a critical infrastructure, and as such, IAM migration projects are fraught with complexity and risk.
In recent years, market-leading IAM products from Oracle and Broadcom (CA Technologies) reached EOL.
With many legacy IAM platforms showing their age and lacking the ability to bridge the gap with newer cloud identity systems, organizations feel the pressure to make migration plans now. The growing use of multi-cloud and hybrid cloud/on-premises infrastructures only adds to the imperative to move off legacy. IT modernization projects are inevitable, and IAM must follow along.
Modernize any app with any IDP in minutes. Join the 'Orchestration Kitchen' workshops.
3 practical steps to transition EOL identity systems to the Cloud
It’s only a matter of time before every organization will need to undertake identity modernization. Here are three practical steps that can be used to plan and control the risk associated with legacy identity migration projects.
Phase 1 – Discover to uncover exposure
The first step to your modernization process is to take stock of which IAM products are currently deployed for your on-premises and cloud resources. This is done through a process known as discovery.
Then, look at the functions your IAM products provide (i.e., user management, single sign-on, authentication, access control, auditing, Java/LAMP apps, Windows .Net apps, etc.) and determine if there are interdependencies.
Taking stock should include performing an inventory of apps grouped by impact and urgency and by what session mechanism (i.e., cookies, headers, SAML, OIDC) is used to pass identity into an app.
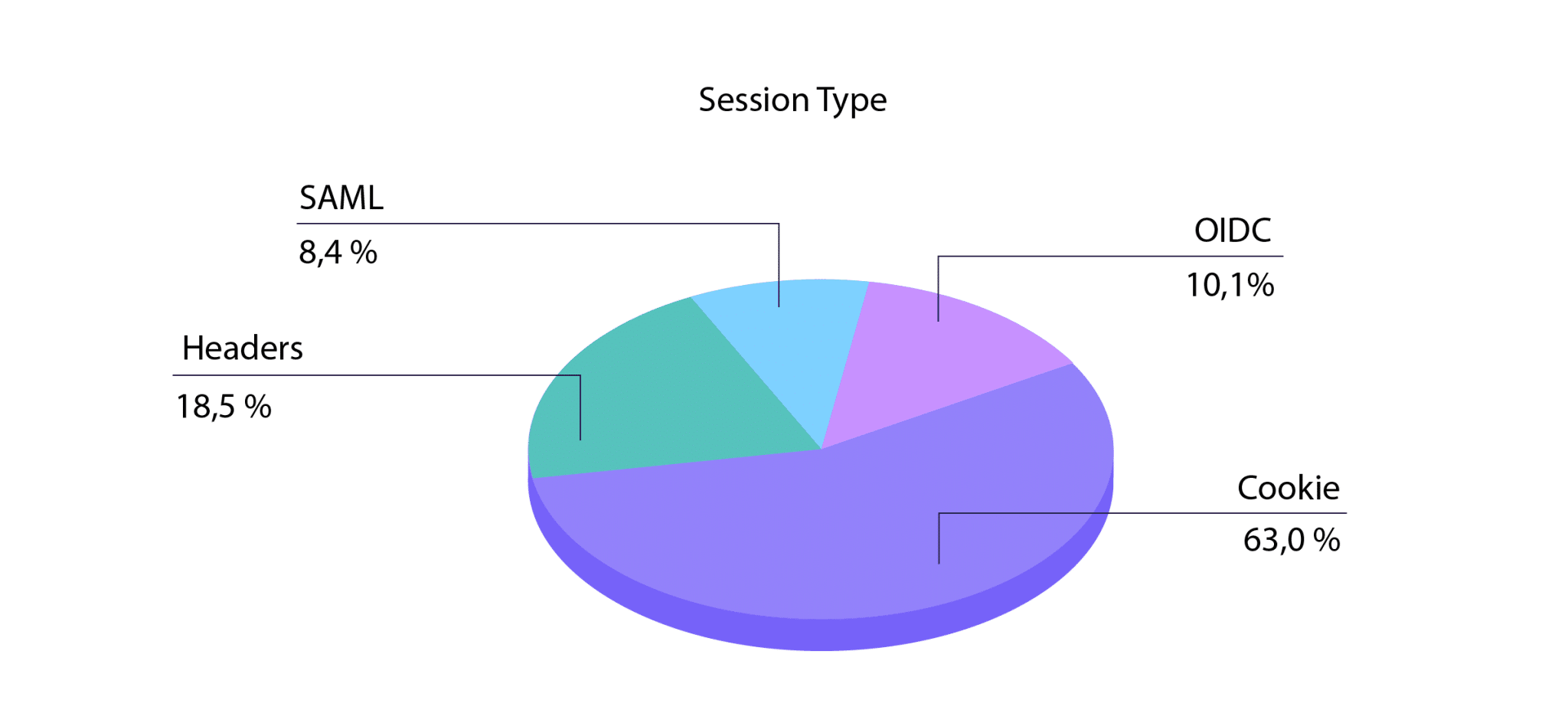 Here’s a sample identity discovery checklist:
Here’s a sample identity discovery checklist:
| Question | Answer |
|---|---|
| What current versions of IAM are running? | |
| what versions of web agents are running? | |
| What apps are currently using legacy IAM software? | |
| What IAM features are currently being used? MFA, Active Responses, custom authentication models, etc.? | |
| What is the network topology and how does it relate to IAM systems? | |
| What is the yimeline for making a swith? | |
| Is there enough time to migrate from one system to another? | |
| Is upgrading to the next version an option? |
Only 10-15% of apps and workloads are on the cloud today, meaning most apps still need to be supported on-premises.
Phase 2 – Plan Identity Migration
Adhere to the “slow down to speed up” mantra to save time in the long run. Here are some important considerations and questions to ask when evaluating modern identity solutions prior to a migration:
- Does the new IAM system have the same functionality and feature set as the one it is replacing?
- What identity repository(s) will be used?
- What session mechanisms are supported, cookie, HTTP Headers, SAML, OIDC, etc.?
- How is policy management performed for controlling roles, groups, and access permissions?
Prepare workflows
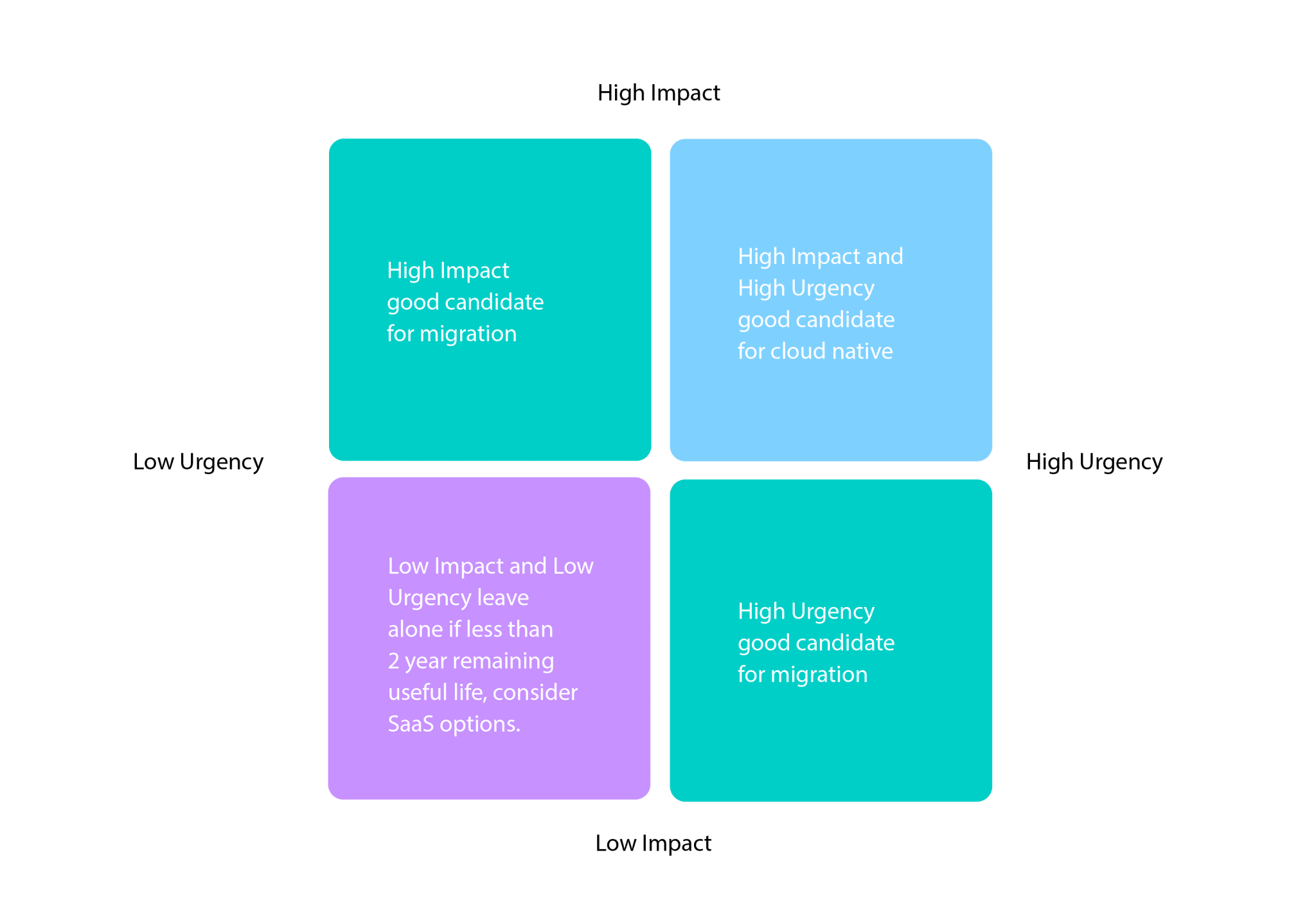
- Organize apps by grouping them according to migration priority and complexity.
- Apply Agile methodology techniques to de-risk migration using small stories, rapid iterations, and test-driven development.
- Rationalize policies and groups where possible.
- Implement a screening process for compromised accounts.
- As much as possible, preserve the UX to reduce concerns over phishing.
- Document dependencies between apps and identity software.
- Map out the network topology to understand how web agents and proxies interoperate with other systems.
Phase 3 – Use Strata’s 5 step process to migrate identities
Moving identities from legacy to a new IAM system is a complex, multi-step process. The following five steps can be used as a guide to help you smoothly transition from on-premises to the Cloud:
- Discover which products are part of your existing identity and app infrastructure — both on-prem and in the Cloud. Then, map out dependencies between apps and identity, including the type of session being used.
- Migrate user accounts and policies from the legacy to the new identity system in real-time. You can harden credentials and accounts at this point too.
- Move apps to the cloud and configure them to talk with the new identity system. Use a migration factory model to move apps at scale.
- Use Secure Hybrid Access to keep some apps on-premises and use cloud identity. Extend MFA to legacy apps so they can use modern authentication without rewrites.
- Retire legacy identity software and decommission unneeded infrastructure to stop paying maintenance and support fees, get out of custom coding migration, and focus on better initiatives.
Digital transformation of business processes using the cloud is already well underway at most organizations. For others, however, planning a migration strategy from legacy to modern identity systems has been on the back burner — often due to complexity concerns.
With EOL on the horizon for most leading IAM platforms, enterprises should begin preparing now if they want to perform a controlled and not a forced move to a modern identity infrastructure.
Become a distributed identity expert
Get the latest articles on all things identity, multi-cloud, and hybrid delivered straight to your inbox



