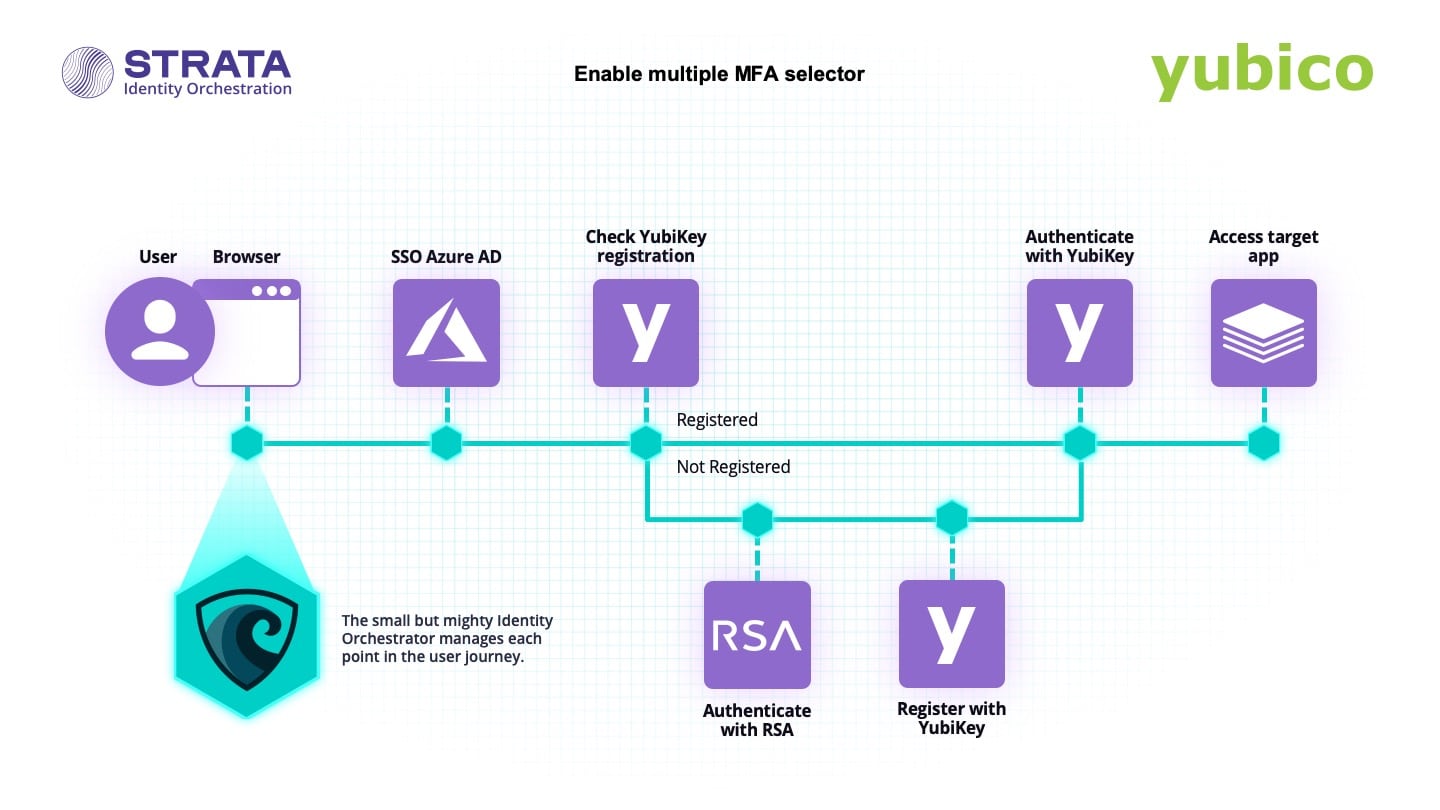
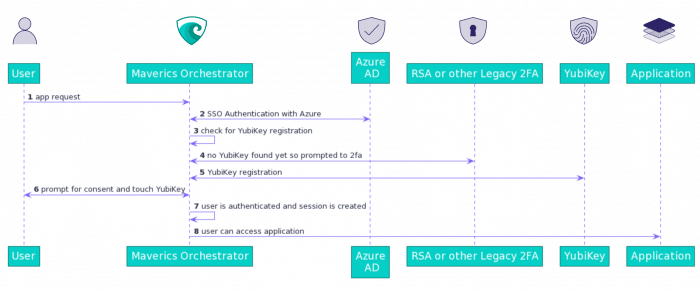
How to enable a multiple MFA selector
Replace legacy RSA SecurID with YubiKey passwordless authentication.
- Replace outdated VPN-centric MFA tokens and adopt modern FIDO2 authentication without custom code
- Enroll users in YubiKey protection without any interruption to existing access workflows
- Enable modern authentication protection for any on-prem or cloud app
Solve more modernization challenges with ready-to-deploy recipes

Keep your employee data sovereign, local and resident. Support your multi-national operations with region-specific IDPs that give users controlled access to common apps.

Still using Active Directory to authenticate users? Secure your legacy mission-critical apps with a modern IDP instead — without refactoring.

Break up with your outdated IDP, keep the complex access policies you love, and replace it with modern authentication and passwordless protection from CyberArk Identity — all without rewriting your apps.
Ready to cook up your perfect identity modernization solution?
Stop juggling disparate identity services. Unleash the power of Strata’s orchestration recipes. Whether you’re dealing with legacy app modernization or controlling multi-cloud access, Orchestration Recipes have got you covered.